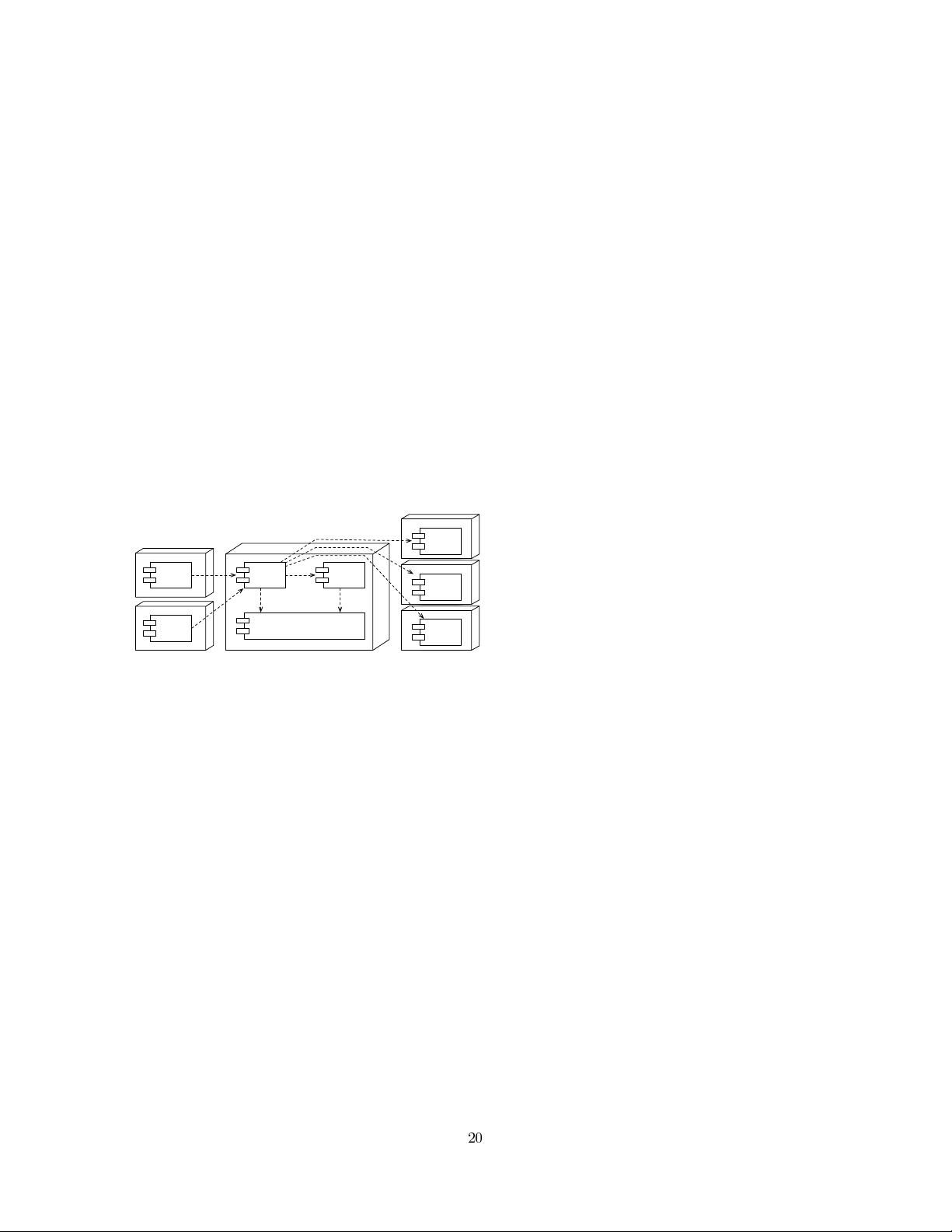
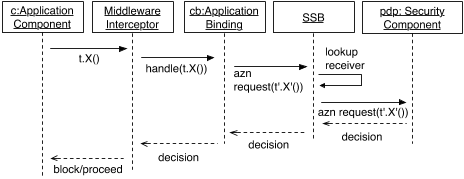
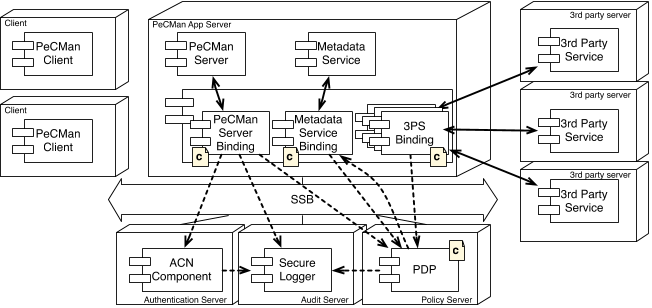
Figure 4: Composing Security Components with
Application Components Using AO Middleware.
The application bindings represent the abstract data model
as interfaces in one of the supported middleware languages.
For instance, if the PeCMan service has the operations up-
dateDocument(document), getDocument(document) and get-
DocumentMetadata(document), the application binding can
have a Document type with read() and write() operations.
AO-based composition can then map the application-level
operations on the abstract operations in the binding.
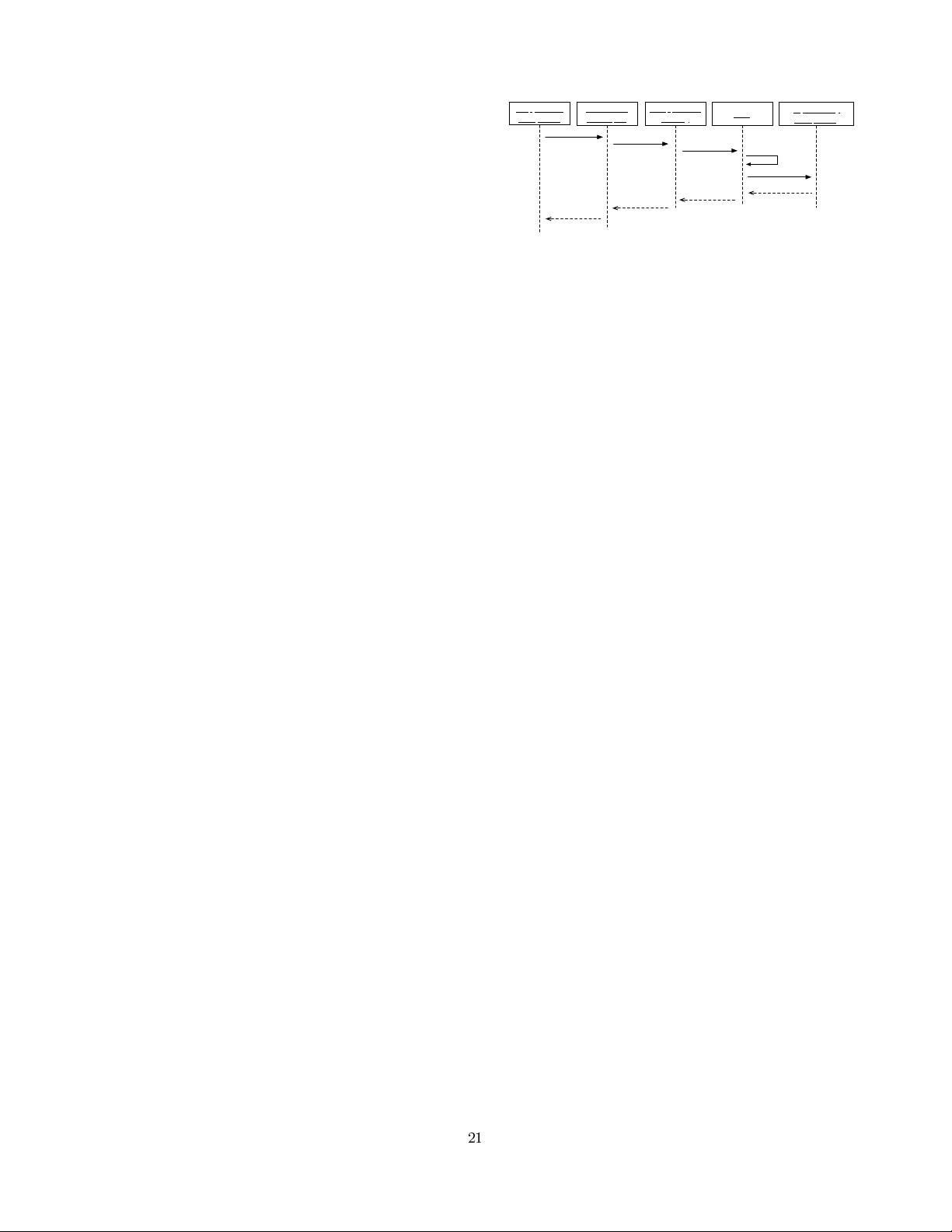
The second kind of composition that can be performed is
the composition between the application binding and the se-
curity components. On AO middleware, this can be realized
by defining an AO-based composition between these com-
ponents in which an invocation to the appropriate security
operation is inserted before the execution of the security-
sensitive operation on the binding. For instance, before the
invocation of read() and write() operations, an invocation
to the checkPermission operation of the authorization com-
ponent is inserted. The pointcut of the aspectual composi-
tion controls when security functionality is invoked. Other
security components can be bound by including the relevant
application joinpoints in the composition for that security
component.
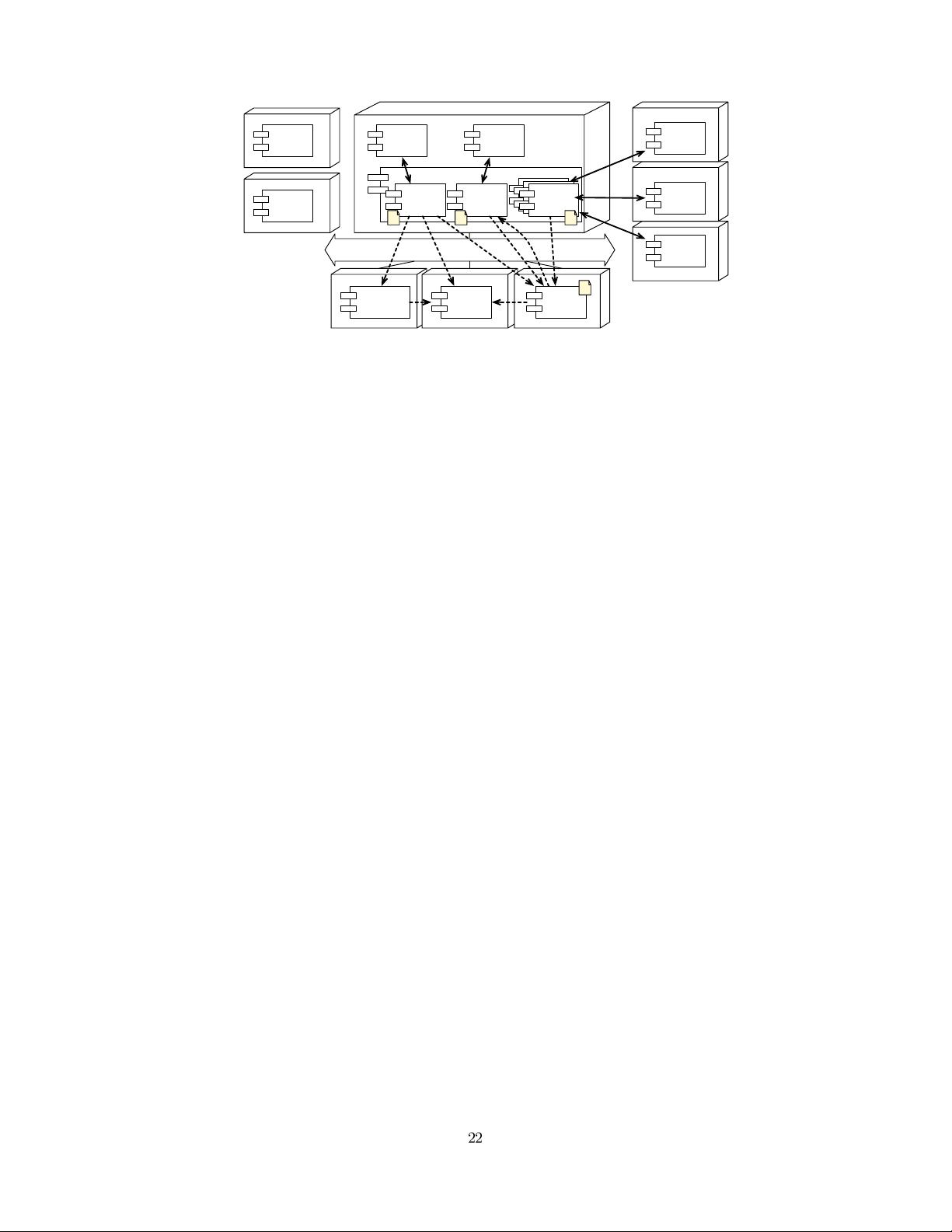
We have illustrated one possible AO-based composition
approach for integrating security components. However,
in more advanced scenarios, such as when mappings get
more complex or when application bindings need to main-
tain state, it might be better to introduce new adaptation
aspects between the composition. Nevertheless, we believe
that in most cases, the approach mentioned above is suffi-
cient.
4.2 Supporting Adaptation
In this section, we revisit the adaptation scenarios for the
case of AO composition.
S1 Adapting local parameters of security components is per-
formed similarly to our approach by invoking an oper-
ation on the security component.
S2 To support a new class of security components, a new se-
curity component implementation should be provided.
S3 (Re-)Composition of a security aspect with other secu-
rity components or with application components is re-
alized by setting or changing the pointcut of the secu-
rity aspect for that component. The kinds of compo-
sitions that can be performed depend on the joinpoint
model of the AO middleware. Due to the very pow-
erful composition model of AOP, it is hard to control
or restrict which security component can be composed
with which application component.
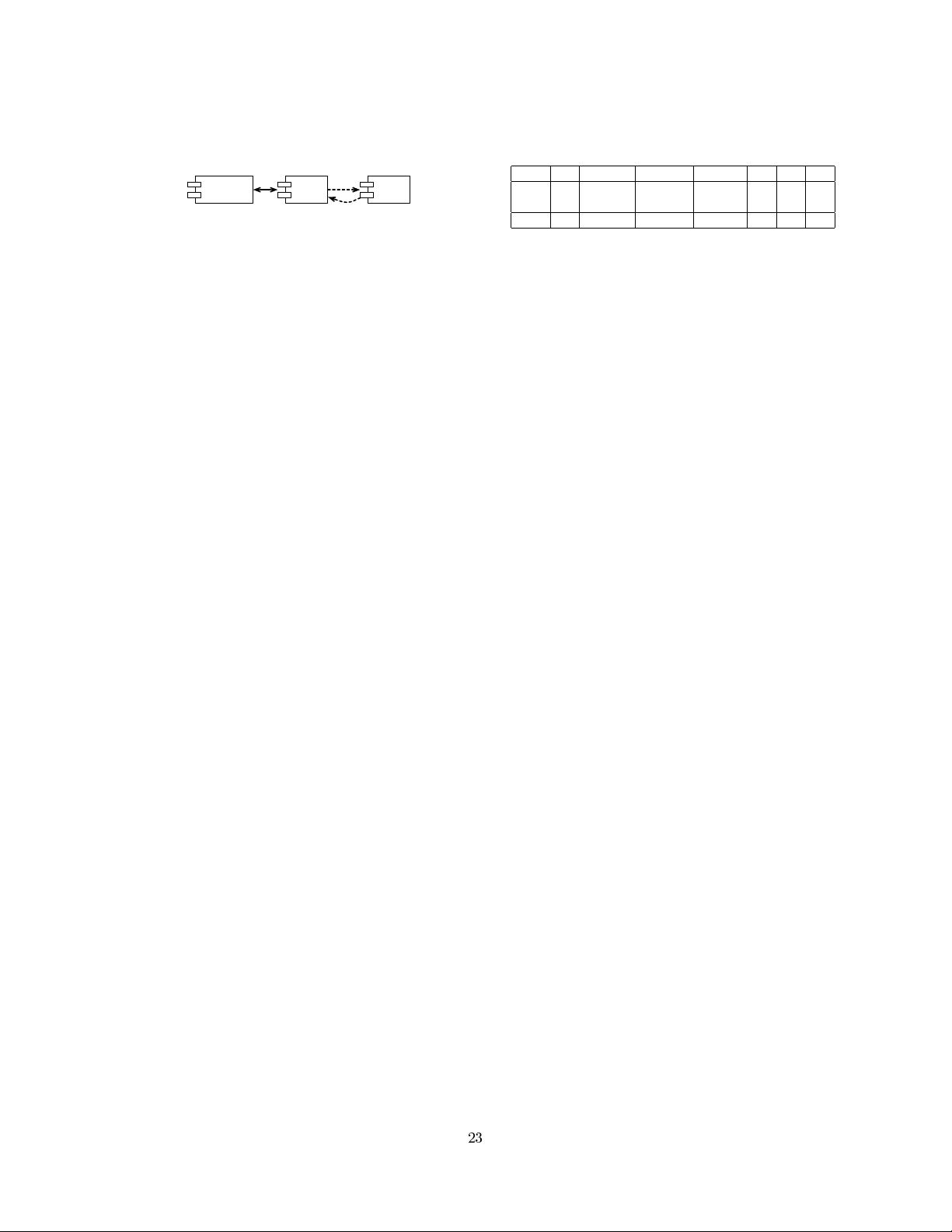
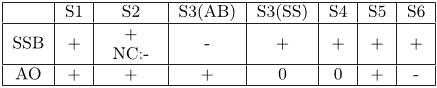
Table 1: Summary of Flexibility Support for Both
Approaches. Legend: support for adaptations is well
(+), neutral (0), bad (−) or bad when a new contract
type needs to e defined (NC:-).
S1 S2 S3(AB) S3(SS) S4 S5 S6
SSB +
+
NC:-
- + + + +
AO + + + 0 0 + -
S4 Replacing an existing security component by one that
adheres to the same interface is done by undeploying
the composition for the original component and replac-
ing it with an advice for the new component that has
the same pointcut(s) as the original aspect.
S5 Since external services fall outside of the control of the
policy enforcing party, proxy components for the ex-
ternal services are needed. If these proxies are not
explicitly part of the application, they typically exist
internally at the middleware level as an endpoint for
the communication protocol. By weaving the security
aspects to these proxy components, security policies
can be enforced.
S6 AO-based composition of security enforcement does not
take into account the effectively required information
from the policies. Therefore, it is hard to support pol-
icy changes. If the new policy needs new application-
level attributes, the policy evaluating component still
needs to invoke the application binding directly.
4.3 Comparison
In this section, we compare how well the adaptation sce-
narios can be supported in both approaches. Table 1 sum-
marizes this. The most straightforward adaptions S1 and
S2 are supported well in both approaches. However, when
a new contract type needs to be defined on the SSB, sub-
stantial manual effort is needed, with the gain of having
additional guarantees on compositions with the new class of
security components. Changes to the composition between
the application component with its binding (S3(AB)) are
harder to support using the SSB approach. In the best case,
only the message interceptions need to be reconfigured, but
it is also possible that the binding component itself has to
be changed. The composition of the binding with the se-
curity components (S3(SS)) is more flexible and easier to
change at runtime using the SSB approach (although this
depends on the runtime changes that are possible on the
AO middleware), and it makes it also easier to reason about
the compositions. The replacement of a security compo-
nent (S4) is possible in both approaches, but in typical AO
middleware platforms, it still requires manual intervention.
Intercepting traffic towards external services (S5) is easy us-
ing interception, but the translation to the abstract policy
model limits its flexibility. In the AO approach, this can
only be supported when there is a local proxy for the remote
component. The security contracts ensure that changes in a
security policy (S6) are easier to support using the SSB.
The conclusions from this comparison are twofold. First,
for the composition between application components and
their bindings, AO is the more powerful alternative over
middleware-level interception. Simple AO platforms often