



Did you find this useful? Give us your feedback












246 citations
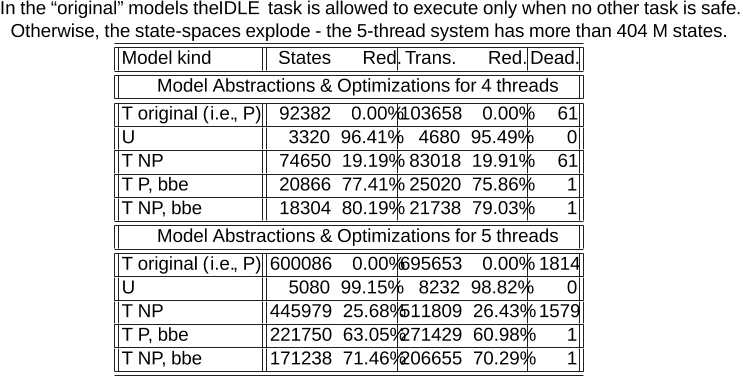
...Nevertheless, its key features, such as combination of behavior and priorities and the resulting advantages in composability and compositionality, have already been positively assessed in some non-trivial applications [18] and [12]....
[...]
43 citations
..., [29]) to make decisions based on available memory resources and the memory-consumption estimates....
[...]
29 citations
...In closely related work, [17, 16] study the synthesis of code-aware managers for Java....
[...]
...This analysis is not present in some recent work on code-aware schedulers [17, 16], a circumstance that prevents those schemes from addressing the problem of progress (or absence of starvation), C compiler C compiler...
[...]
29 citations
26 citations
121 citations
103 citations
..., [10,17]) to generate executable code for a run-time system and to provide a native implementation of the real-time primitives....
[...]
90 citations
...In order to obtain more precise semantics, domain-specific profiles have also been defined, such as the Ravenscar-Java [8] high-integrity profile for safety-critical systems....
[...]
...Besides, we have a non-POSIX prototype implementation overCos that uses alarms and alarm handlers, thus allowing us to support deadline and period miss handlers as proposed by the RTSJ, but disallowed by the Expresso and the Ravenscar-Java profiles....
[...]
...Our work is based on the two/three-phase execution model and API of the Expresso High-Integrity Profile [4], which itself inherits concepts from the Ravenscar-Java profile and the RTSJ API....
[...]
60 citations
...Following [13], we first extract a formal model of the behavior of the application program as an extended automaton (see Fig....
[...]
41 citations
...1 Architecture The architecture of the schedulers we synthesize consists of two three-layered stacks [7], as shown in Fig....
[...]