



Did you find this useful? Give us your feedback














10,755 citations
...Generally Petri nets focus on specific properties such as liveness, deadlock, livelock, boundedness and safeness [9-11]....
[...]
...It is used as a visual communication aid to model concurrency, synchronisation, limited resources, sequentially, mutual exclusion and behaviour in distributed systems [9-11]....
[...]
...The formal definition of a Petri net is shown in Table 1 [10]....
[...]
...In other words, a Petri net must consist of the following components [9-11]:...
[...]
6,902 citations
2,523 citations
...The concept of the Petri net [7] was introduced in 1962 by Carl Adam Petri [8]....
[...]
308 citations
...Sometimes it may involve a trusted third party to operate the authentication and validation, such as the Kerberos login protocol [1], while other systems deploy biometric automated verification systems to recognise trusted users....
[...]
...Typically cryptographic protocols, also known as security protocols, tend to inhabit a complex environment by utilising various cryptographic mechanisms, such as symmetric and asymmetric encryption, hash functions, timestamps, and digital signature [1]....
[...]
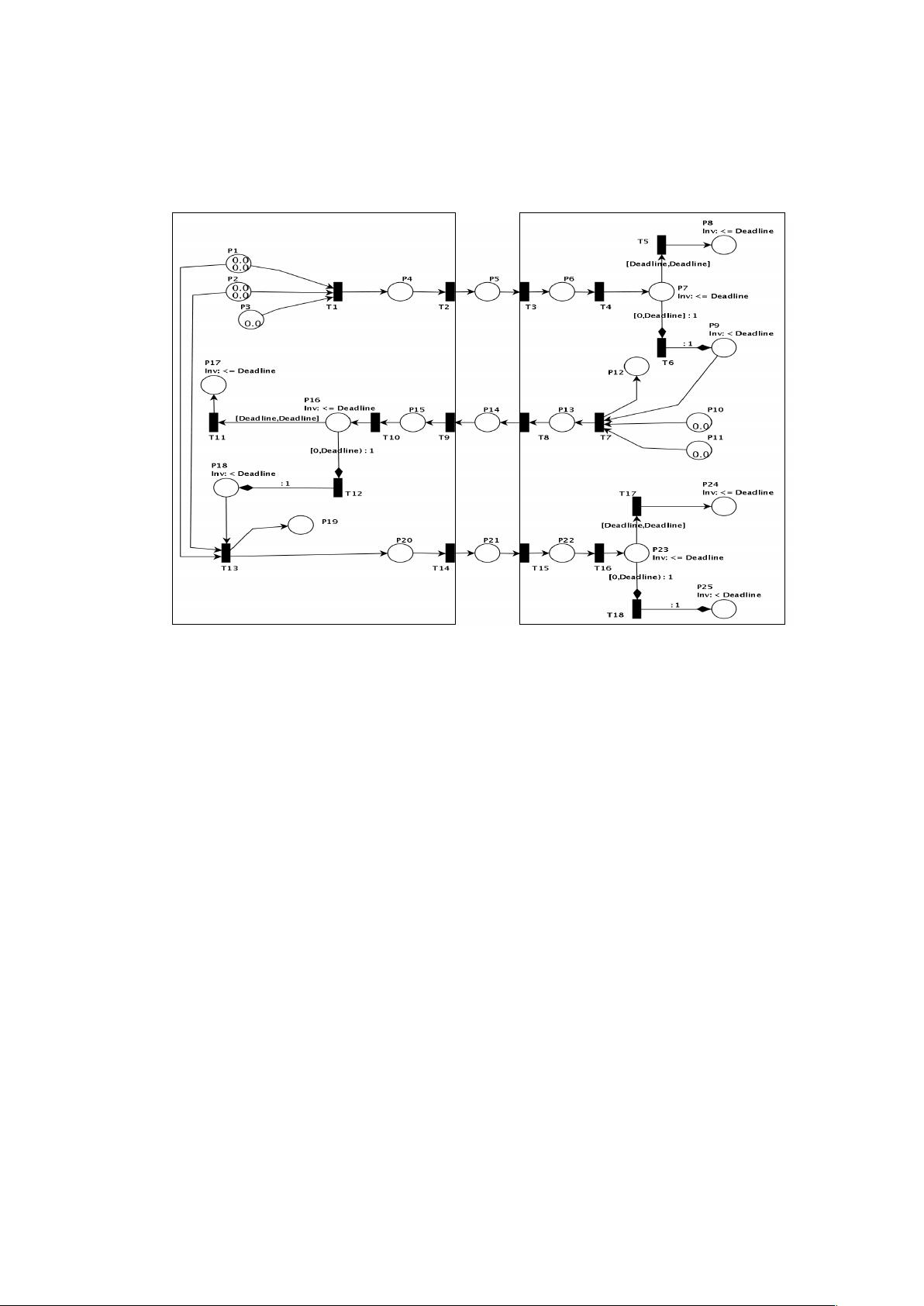
A Petri net is defined as a bipartite directed, weighted graph with two types of nodes called places and transitions, linked by directed arcs.
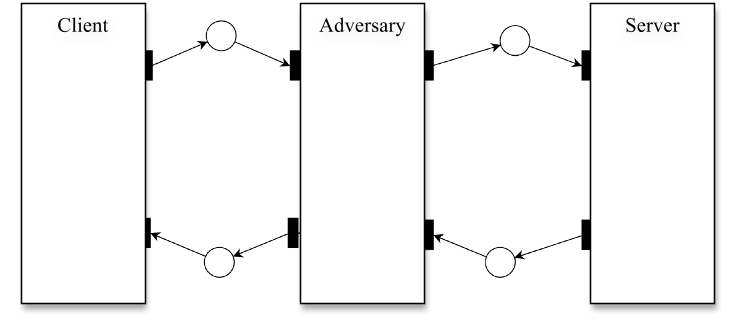
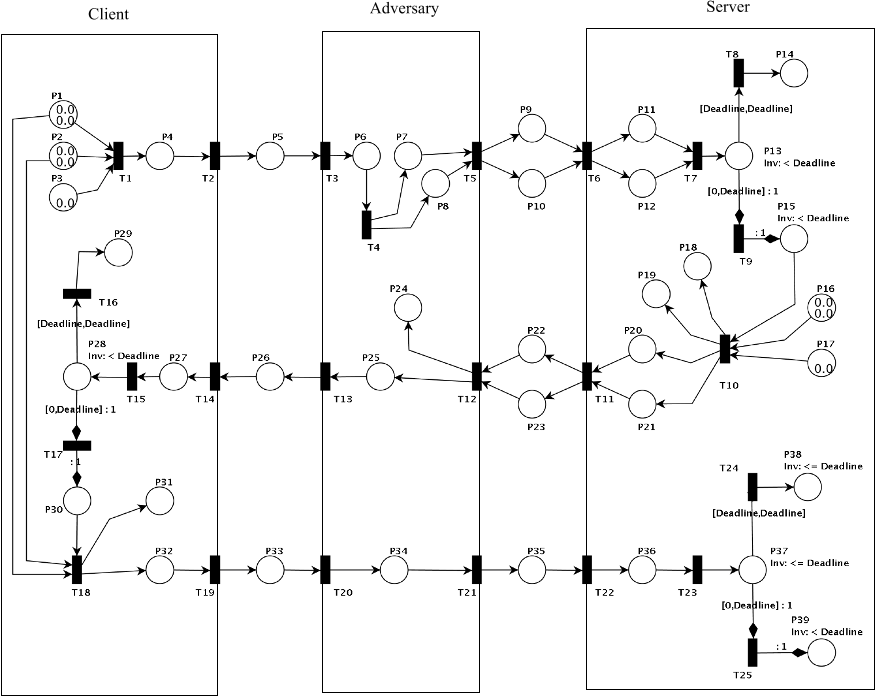
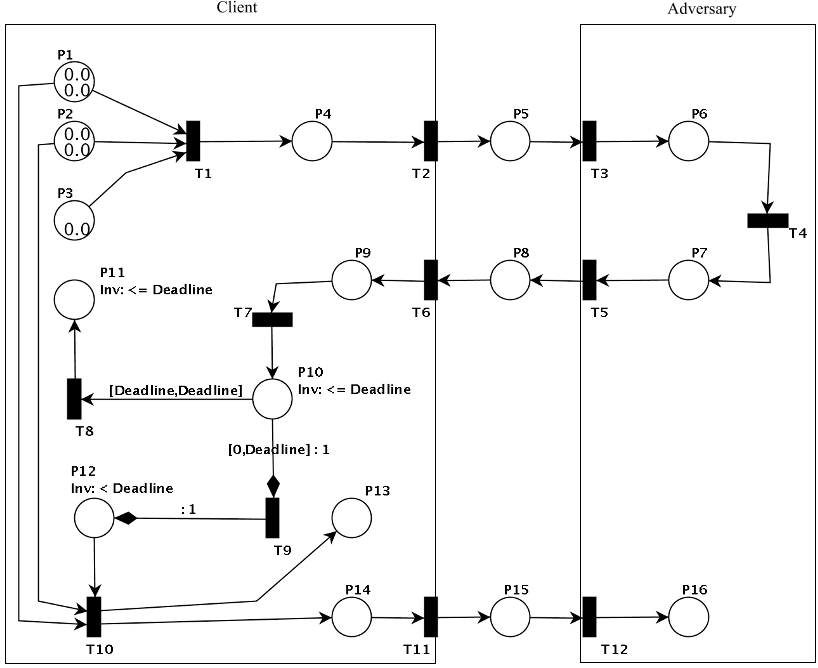
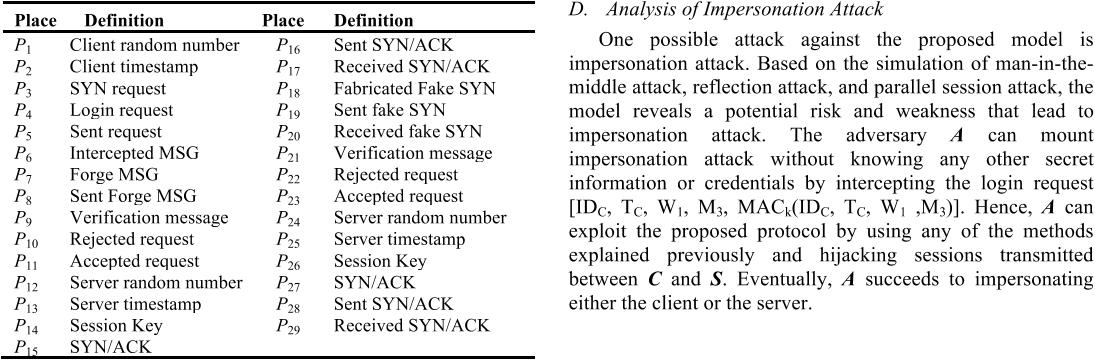
The main goal of the adversary model is to examine the protocol behaviour with the presence of an adversary while modelling attacks.
It is evident that the most viable countermeasure to defend authentication attacks is to encrypt the message exchange between the client and server.
the adversary entity is nondeterministic, in that it may perform different possible actions under different client identities at a given time to ultimately compromise the target system.
Sometimes it may involve a trusted third party to operate the authentication and validation, such as the Kerberos login protocol [1], while other systems deploy biometric automated verification systems to recognise trusted users.
(1) The likelihood of correlation associated with T –̀ TC ≤ ∆T will be high considering the time-delay in widearea networks is unpredictable and varies most of the time.
Each attack scenario has been simulated using PN to exploits vulnerabilities in case if the symmetric encryption was not applied to their new protocol.
A instantly impersonates C and initiates a new session with S by sending a fabricated login request: P19 = [IDA =ID`C , TA = T`S, W1=W`2, M3 = M`6, M7, MAC`k(IDC, TS, W2, M6, M7)], which is S original reply to C.Assume if the fabricated message arrives to S at time T, it will pass the verification check for the following reasons:
To exploit the reflection attack, the adversary A intercepts the login request while listening to the electronic conversation between client C and server S. Then, the adversary sends the same login request [ID`C, T`C, W`1, M`3, MAC`k(IDC, TC, W1 ,M3)] to C in a timely manner.