A New Biometric ID-Based Cryptography Protocol
and Security Analysis Using Petri Nets
Dania Aljeaid
School of Science and Technology
Nottingham Trent University
Nottingham, United Kingdom
N0360890@ntu.ac.uk
Xiaoqi Ma
School of Science and Technology
Nottingham Trent University
Nottingham, United Kingdom
xiaoqi.ma@ntu.ac.uk
Caroline Langensiepen
School of Science and Technology
Nottingham Trent University
Nottingham, United Kingdom
caroline.langensiepen@ntu.ac.uk
Abstract—This paper presents a Petri net (PN) approach to
modelling, simulating, and analysing the new protocol we have
proposed. This new protocol is an enhanced authentication
scheme based on a biometric verification mechanism and identity
based cryptography. A formal approach like Petri nets allows one
to represent cryptographic protocols. For the sake of simplicity, a
complex PN model will not be discussed in this paper until all
attacks are demonstrated and the model proved to be secure.
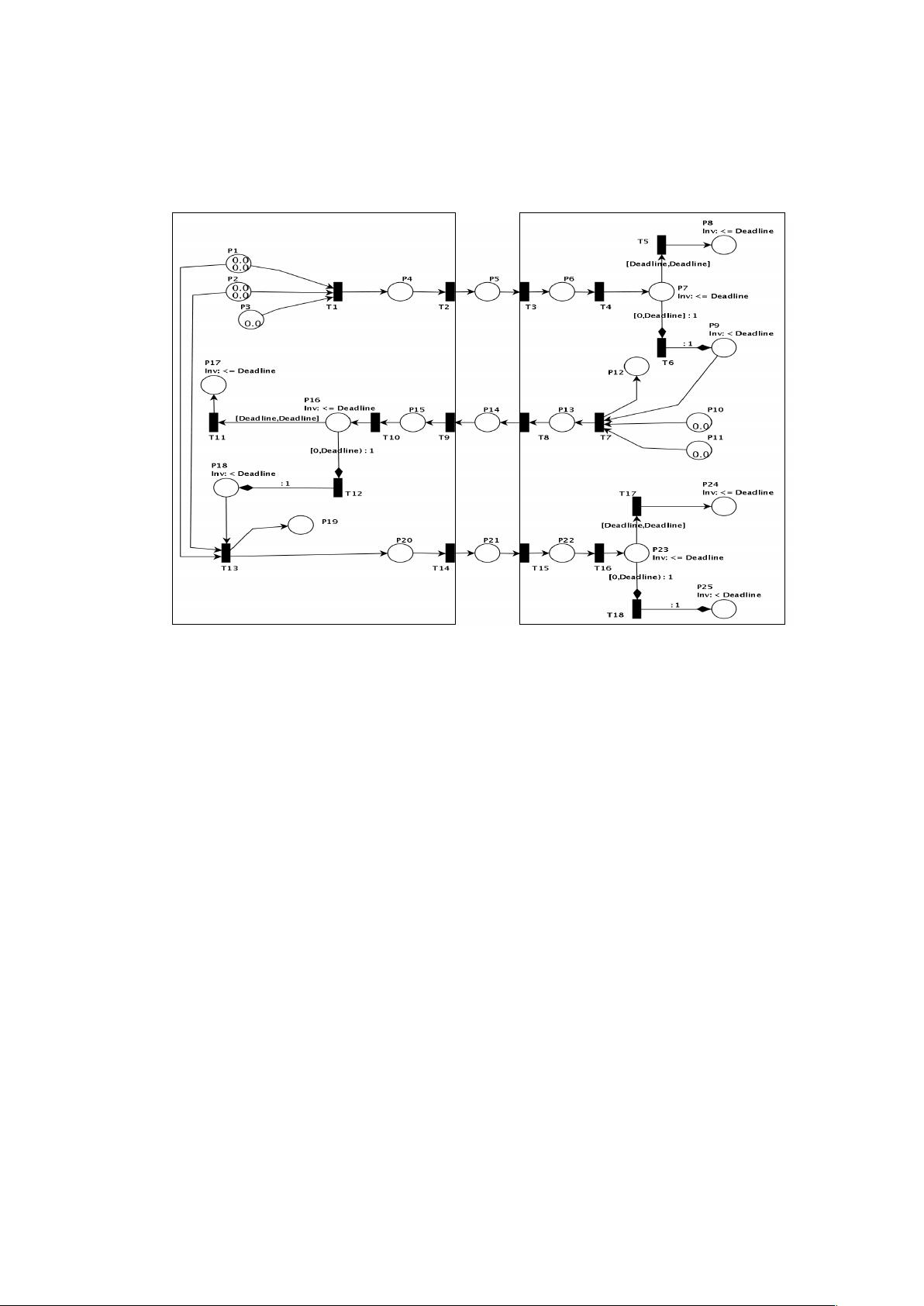
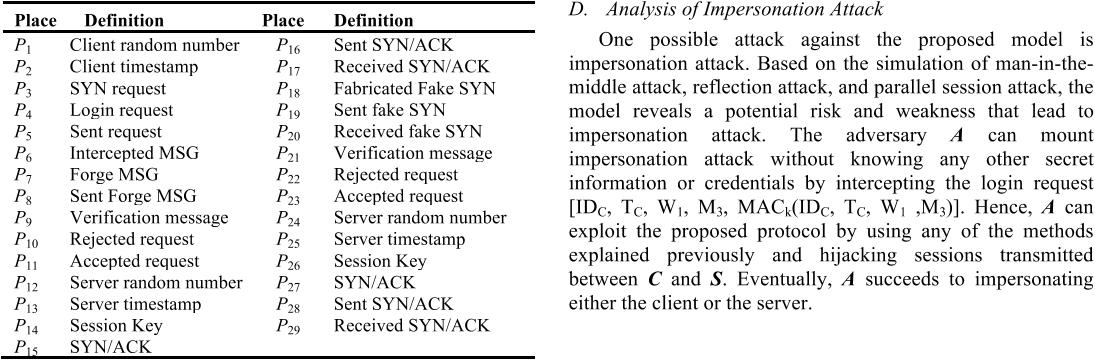
This paper shows how Petri nets are used to model, analyse and
detect flaws in our new protocol. First, our proposed protocol is
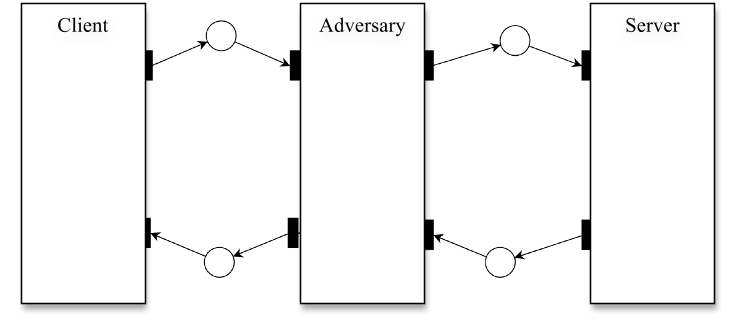
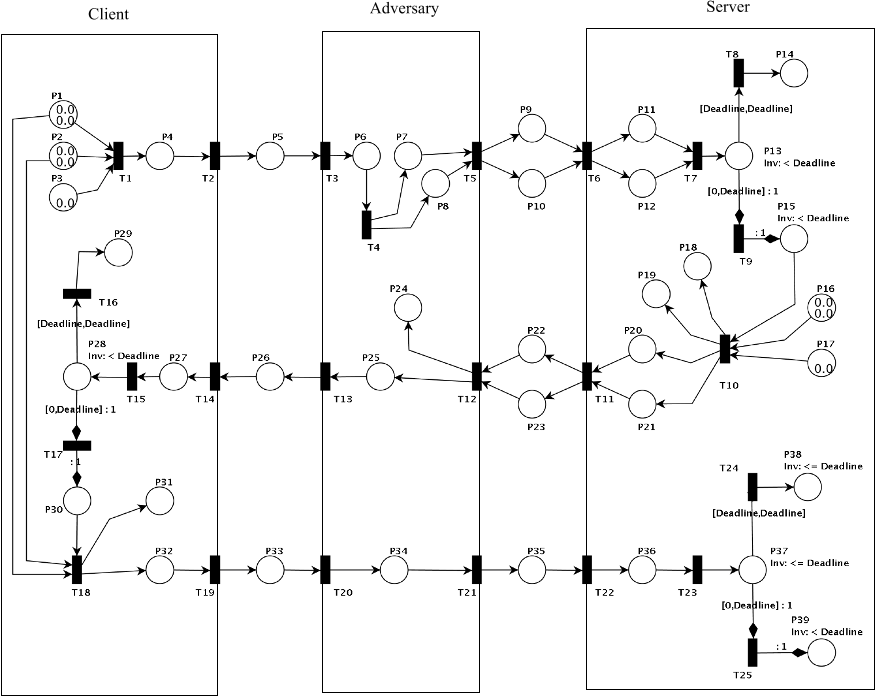
modelled without an adversary, and then a generic adversary
model is added to examine all possible adversary behaviours.
Finally we demonstrate how Petri nets can be used to analyse
security threats such as man-in-the-middle attack, reflection
attack, and parallel session attack on this protocol.
Keywords- identity-based cryptosystem; biometrics; security
analysis; cryptographic protocol; Petri nets.
I. INTRODUCTION
Due to the unique characteristics possessed by
cryptographic protocols, analysis and evaluation tend to be
more difficult than normal protocols. Typically cryptographic
protocols, also known as security protocols, tend to inhabit a
complex environment by utilising various cryptographic
mechanisms, such as symmetric and asymmetric encryption,
hash functions, timestamps, and digital signature [1]. For this
reason, Petri nets offer the opportunity to conduct an in-depth
analysis and overcome security vulnerabilities and weaknesses.
Moreover, they simplify the modelling of exchange messages
between nodes and describe behaviour of authentication and
key agreement procedure. A number of researchers have used
Petri nets to model and analyse cryptographic protocols [2 -6].
The structure of this paper is organised as follows. In
Section 2, we briefly review previous works on Petri nets and
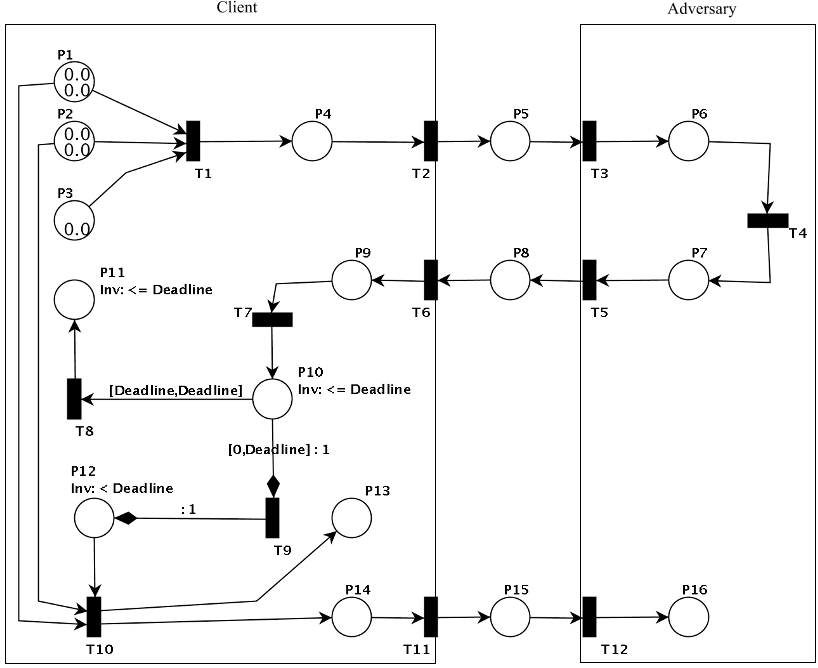
our new protocol. In Section 3, we model the client-server
trust model using PN. In Section 4, we add the adversary
entity to the trust model and simulate various attacks using
PN. We then provide a brief discussion on security analysis in
Section 5. Finally, the conclusions are given in Section 6.
II. REVIEW OF RELATED WORK
A. Petri Nets
The concept of the Petri net [7] was introduced in 1962 by
Carl Adam Petri [8]. Petri nets are graphical diagrammatic tools
based on strong mathematical foundations. It is used as a visual
communication aid to model concurrency, synchronisation,
limited resources, sequentially, mutual exclusion and behaviour
in distributed systems [9-11]. A Petri net is defined as a bipartite
directed, weighted graph with two types of nodes called places
and transitions, linked by directed arcs. In other words, a Petri
net must consist of the following components [9-11]:
! A set of places (drawn as circles in the graphical
representation), represent conditions and possible states
of the system.
! A set of transitions (drawn as rectangles or thick bars),
represent a change of state which caused by events or
actions
! A set of arcs (drawn as arrows), connecting a place to
transition and vice versa.
! Tokens (drawn as black dots), occupy places to
represent the truth of the associated condition.
The formal definition of a Petri net is shown in Table 1 [10].
Generally Petri nets focus on specific properties such as
liveness, deadlock, livelock, boundedness and safeness [9-11].
Table 1. Formal Definition of a Petri Net
A Petri net is 5-tuple, PN=(P,T,F,W,M
0
) where:
P={p
1
, p
2
,…,p
m
} is a finite set of places,
T={t
1
,t
2
,…,t
n
} is a finite set of transitions,
F (P X T) U (T X P) is a set of arcs (flow
relations),
W: F " {1, 2, 3,…} is a weight function,
M
0
: P " {0, 1, 2, 3,….} is the initial marking,
P ∩ T= ø and P U T ≠ ø.
A Petri net structure N=(P, T, F, W) without any specific initial
marking is denoted by N.
A Petri net with the given initial marking is denoted by (N, M
0
).