




Did you find this useful? Give us your feedback












44 citations
2 citations
...In this thesis, in Paper E which extends our earlier work [64], we study how anonymity networks could be used to improve the data availability if face of gray hole attacks....
[...]
1 citations
...Minstrels, described in [6], uses nodes as message relays in the same way as Crowds with the difference that the number of nodes visited by a message is bounded....
[...]
...A detailed description of calculating Prel(s,r) can be found in [6]....
[...]
...Second, Minstrels, proposed in [6], which provides bounded message delivery delay by limiting the maximum number of visited nodes for each message, and hides the sender and the receiver among all anonymity network users....
[...]
853 citations
523 citations
382 citations
...Many communication systems, for example modern industrial networks [ 1 ], [2], require high availability between a fixed set of nodes on a pairwise basis....
[...]
228 citations
...We do not consider long term intersection attacks, such as [8], [9], [10], which exploit cases when the sender’s anonymity is not beyond suspicion, i....
[...]
213 citations
..., by making it untraceable who communicates with whom [4]....
[...]
It is subject of their future work to provide a more complete characterization of the overhead-anonymity trade-off for anonymity networks, including networks that provide probabilistic message delivery.
To control the maximum path length (i.e., delay) the sender can initialize the list of visited nodes with a number M ∈ {0, ...,N−1} of the nodes in the system.
Since the traffic matrix is homogeneous and attackers are informed about each other, all trusted nodes are equally likely to be the sender, P(S(s)) = 1N−C , and any trusted node (except the sender) is equally likely to be chosen as the receiver, i.e., with probability P(R(r)|S(s)) = 1N−C−1 .
The reason is that as the number of relays increases the probability P(H1+) of having an attacker on the path increases faster than the certainty of the attacker about the identity of the sender-receiver pair decreases.
while for Minstrels the relationship anonymity decreases above a certain level of overhead, for Crowds the relationship anonymity improves monotonically.
The attacker can only decrease the relationship anonymity by knowing the protocol and by observing traffic that goes over the nodes it controls.
The reason is that for N = 50 the attacker appears later on the path than for N = 10 so the sender does not appear as predecessor that often.
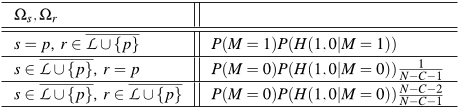
In Minstrels the probability that the attacker assigns to a sender-receiver pair does not only depend on the node that the message is received from, i.e., the predecessor p, but also on the contents of the list of visited nodes (L) that the message carries.
5. Relationship anonymity vs. overhead for N = 50, C = 5bounds converge to an asymptote, which corresponds to the case when there is always an attacker on the path (P(H1+) = 1), and the attacker assigns Prel(s,r) = 1(N−C)(N−C−1) to every possible sender-receiver pair.
Given a message received by an attacker that contains information (||L || = l, ωs ∈ Ωs, ωr ∈ Ωr, and MC = mC) the attacker would identify (s,r) as the sender-receiver pair with probabilityP(R̂(r), Ŝ(s)|ωr,ωs,mC,H1+, l) = P(ωr,ωs, l,mC,H1+|S(s),R(r)) ·P(R(r)|S(s)) ·P(S(s)) ∑(a,b) P(ωr,ωs, l,mC,H1+|S(a),R(b)) ·P(R(b)|S(a)) ·P(S(a)) (11)where the summation in the denominator is over all possible non-attacker sender-receiver pairs (a,b). P(S(s)) is the (a priory) probability that node s sends a message, and P(R(r)|S(s)) is the probability that node s selects node r as the destination of a message.
The relationship anonymity provided by Crowds is significantly worse than the lower bound, which is primarily due to the lack of receiver anonymity.
The mean number of hops for Crowdsis the expected value of a geometric distribution with success probability 1− p f , i.e.,E[K] = p f1− p f +2 (2)where p f is the probability that a node will relay a message.
if the sender is the predecessor (s = p) then the receiver cannot be in the list of visited nodes (r ∈ L \\ {p}), because this could only happen if the sender had prefilled the list of visited nodes with the receiver, but then the receiver would never receive the message.
Crowds: For Crowds the first attacker is on position i if the message is first relayed i−1 times through trusted nodes but the last hop is an attacker.