



Did you find this useful? Give us your feedback













943 citations
...Data dissemination protocols [6], [ 7 ] have been proposed to disseminate information about traffic, obstacles, and hazards on the roads....
[...]
666 citations
...Data dissemination protocols [6], [7] have been proposed to disseminate information about traffic, obstacles, and hazard on the roads....
[...]
623 citations
...However, directionalized antennas increase the number of hidden nodes and, as shown later, have an adverse affect on intrusion-detection systems....
[...]
398 citations
293 citations
...[41] has proposed an opportunistic resource discovery protocol with a finite-buffer space model....
[...]
4,355 citations
4,278 citations
2,525 citations
2,375 citations
2,035 citations
However, another possibility which the authors plan to investigate in future research, involves query delivery to all the vehicles in a geographic area, and the collection of results.
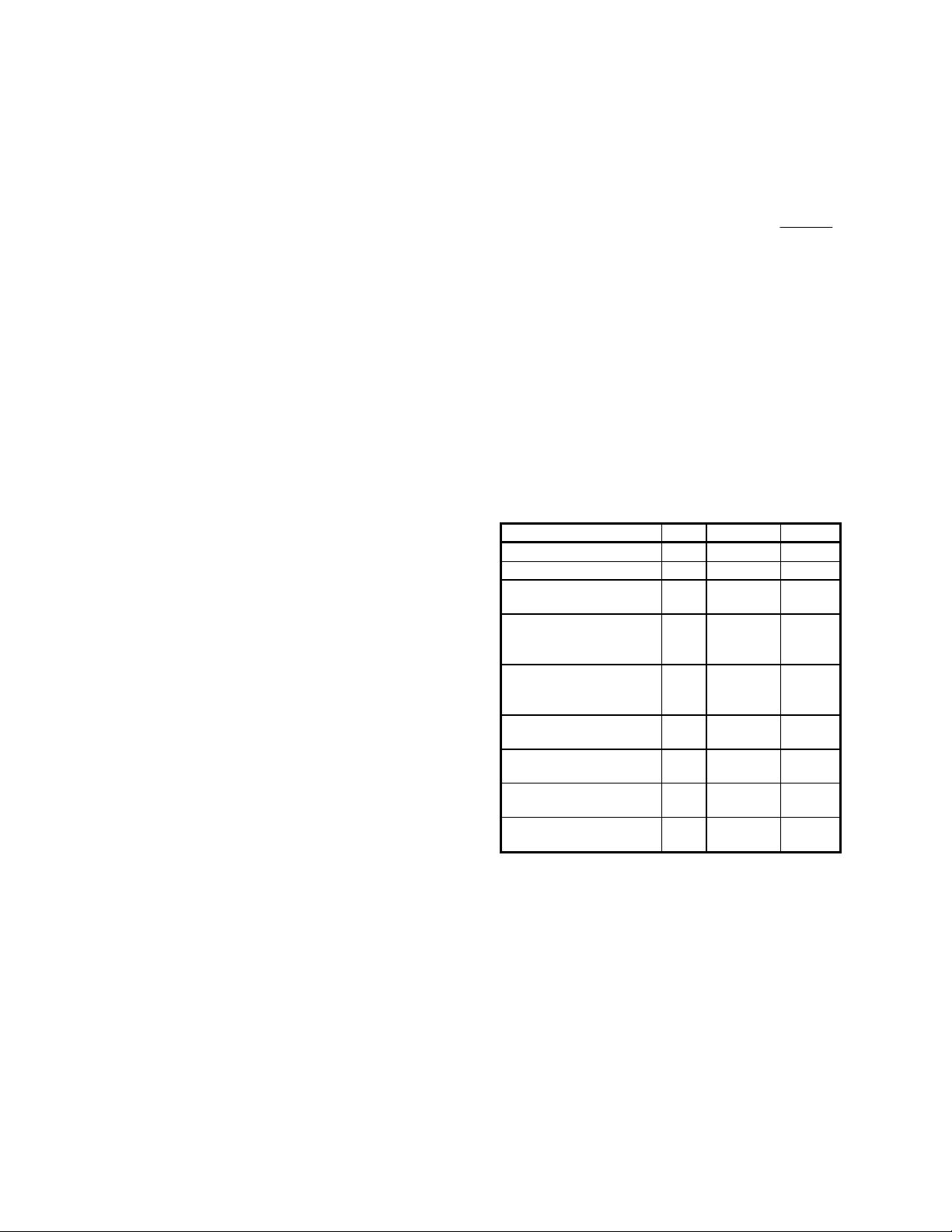
There are three parameters for each simulation run, namely the memory allocation M, the transmission range r, the constant speed v, and the traffic density d (i.e. the number of objects per square mile).
The analysis suggests that the opportunistic exchange algorithm automatically restricts the propagation of a resource to a limited spatial area and a limited temporal interval.
Since R is rejected or purged by O at t, the relevance of the least relevant resource in O s memory at t cannot be lower than)()( 00 ttvtt −⋅⋅−−⋅− βα .
If an object happens to travel a relatively long distance without interacting with any other object, then the boundary radius for a resource it carries will have a jump.
An increased transmission range results in a vehicle receiving a greater number of resources in a given time interval, thus causing greater contention for thememory, and causing entries to be bumped out of the memory sooner.
Typically these architectures consist of a dedicated directory agent that stores information about different services or data, a set of protocols that allows resource providers to find a directory agent and to register with it, and a naming convention for resources.
as the traffic density increases, a vehicle receives new resources more frequently, and therefore a resource is likely to be purged sooner.
Because the relevance of a resource for a moving vehicle is dynamic, a vehicle may refuse a resource at one time and then later find it of interest.
In this paper the authors devised a model for discovery of spatio-temporal resources in an infrastructure-less environment, in which the database is distributed among the moving objects.
During a simulation run, the authors trace the distribution of each resource R at each time unit during R s lifetime (R s lifetime is the time period from the time when R is generated up to the time when it disappears from the system).
If R is rejected or purged by an object O at time t (t≥t0), then at any time point t after t, the relevance of the least relevant resource in O s memory is higher than or equal to )'()( 0ttv −⋅⋅+− βα .Proof: Consider the relevance of R to O at time t. Since R is created at t0 and the transmission range is 0, the distance between the location of O at t and the home of R cannot exceed )( 0ttv −⋅ .
It can be seen from Figure 6 that, (i) with a bigger transmission range, the coverage of a resource expands to the maximum value sooner; (ii) as the size of transmission range increases, the length of lifetime decreases.
According to Lemma 1, the relevance of the least relevant resource in O s memory at t is higher than or equal to)()()( 0 vK Mttv ⋅+⋅−≥−⋅⋅+− βαβα .
It can be seen from Figure 5 that, (i) with higher memory allocation, the coverage of a resource expands to a higher maximum value and it expands to that value later; (ii) as the memory allocation increases, the length of the lifetime increases.
It can be seen from Figure 7 that, as the traffic speed increases, the coverage of a resource expands to the maximum value sooner and the length of lifetime is shorter.
If R is received by an object O at time t (t≥t0), then at any time point t after t, the relevance of R for O at t is not lower than )'()( 0ttv −⋅⋅+− βα .Proof: Consider the relevance of R to O at time t. Since R is created at t0 and the transmission range is 0, the distance between the location of O at t and the home of R cannot exceed )( 0ttv −⋅ .
Now the authors prove that at any point in time, there is no copy of R at any location that is more than K Mv ⋅ distance units away from the home of R. Consider the relevance of R for an object O that is more thanK Mv ⋅ away from the home of R.