Pushing using compliance
Summary (4 min read)
1 Introduction
- Over the years various techniques have been developed that address the problem of navigating through or interacting with a real or virtual world.
- Objects can be manipulated in numerous ways, and each type of manipulation implies different constraints on the combined motion of manipulator and object.
- Compliance has often been used to compensate for uncertainty, for example to solve the peg-in-hole problem.
- Next, the pre-image is iteratively treated as a new goal until the initial robot configuration is within a pre-image.
- While being pushed by the pusher, the object is allowed to slide along the boundary of the environment (compliant motion).
2 Preliminaries
- In this paper it is assumed that P always keeps contact with O (see the conclusions for some remarks on this).
- It is assumed that the friction between O and the supporting plane is large enough such that there is no motion of O after pushing ceases (quasi-static assumption).
- At compliant position q ∈ Rroγi , the push range describes the continuous range of push positions that cause O to follow the same path (regardless of the push position being collision free).
- Given a compliant configuration, the authors define the bounding obstacles (Fig. 6).
- A hockey stick curve minimizes the distance needed to push O away from an obstacle.
3 Rapidly-exploring Random Trees
- Many motion planning algorithms are based on the generation of collision-free samples.
- Between these, connections are tried and a graph is formed that can be used to solve motion planning queries.
- Retracting non-compliant samples to the obstacles [2] seems a straightforward solution.
- After a random sample has been created, most algorithms try to connect it to already existing samples in the graph.
- The authors will first briefly explain how the basic RRT algorithm works and then elaborate on how to adapt the RRT such that it is suited to solve their problem.
3.1 The basic RRT algorithm
- The RRT is a single shot approach in which a tree is constructed that gradually improves resolution.
- Here, the authors will use the bidirectional version of the RRT that grows two exploration trees:.
- As the trees grow larger, the two trees are more likely to connect.
- The advantage of the bidirectional version over the single directional version is that it is better at escaping local minima.
- If c′c = cc, the two trees are connected and a solution is found.
3.2 Tailoring the RRT
- The basic RRT algorithm is not suited for pushing problems since it does not incorporate the role of P .
- If obstacles belong to the same compliant component, a path through compliant space may exist between them.
- Because of the physics of pushing, pushing motions are irreversible.
- As a result, the connections between vertices of the RRT are directed and the paths the local planner creates are only suited for motions in one direction.
- If a compliant configuration is involved, the shortest distance between two configurations may however consist of a hockey stick curve.
4 Local Planner
- It connects two configurations to each other, usually by trying a straight line path between them.
- Also the authors need two versions of the local planner: a “forward” one (Algorithm 2) and a “reversed” one (Algorithm 3); both will be discussed.
4.1 Forward local planner
- The authors will consider the various types of local paths necessary to create the local planner.
- Suppose the nearest neighbor configuration cn resulting from line 5 of Algorithm 1 is non-compliant (Fig. 11a).
- It is likely that this will fail because γi will probably impede the contact transit.
- If this succeeds, the authors are certain that P now fits between O and γi.
- Before the end of the hockey stick is reached, P may encounter another obstacle.
4.2 Reverse local planner
- A straightforward solution would seem to use the same local planner and just reverse the endpoints (starting at qc and moving to c ′ n).
- Because of the above considerations, the authors need a true reverse version of the local planner.
- Therefore it makes no difference whether c′n is non-compliant (Fig. 11d) or compliant (Fig. 11e).
- In that case, the algorithm ends successfully.
- The third situation that can occur is that P collides with obstacle γi (Fig. 11g).
4.3 Geometric primitives
- The task of the local planner is to verify if the random position qr can be reached from the nearest configuration cn = (qn, αn) in the tree or else report the first obstacle with which there will be a collision.
- To solve this, the authors will transfer this problem to basic geometric problems.
- Ray shooting considers the problem of determining the first intersection between a ray (a directed line segment) and a collection of obstacles.
- Note that both the clockwise and counterclockwise contact transits for P need to be checked.
- Because it is not essential to find the nearest neighbor configuration exactly and because their edges do not solely consist of straight lines (but also hockey stick curves), the authors can use an approximate solution.
5 Compliant exploration
- If the local planner is not able to reach the random configuration qr but instead hits an obstacle γi at configuration cc, this collision point is used as a starting point for compliant exploration.
- Compliant exploration is a procedure to capture the topological structure of the set of compliant configurations that can be reached starting at cc, i.e. the part of compliant space that can be reached.
- The results of this exploration are compliant configurations that are added to Ts and Tg. Starting at cc, the authors initiate the compliant exploration in two directions: clockwise and counterclockwise; for one of these a preceding contact transit is necessary.
- To capture the topology of compliant space and to distinguish between explored and not yet explored parts of compliant space, intervals are used (see Definition 2.4).
- Therefore, v does not represent a single position, but rather the continuous subset [qcc , qe(Iγi)] of Iγi .
5.1 Forward compliant exploration
- If the RRT algorithm generates a compliant configuration cc = (qcc, αcc) on obstacle γi, the corresponding interval Iγi is identified by determining the bounding obstacles.
- The first case occurs if Iγi has not been encountered before.
- If a new vertex v has been added to Ts, the authors check whether, at position qe(Iγi) the next interval can be reached (possibly after a contact transit).
- Since P and O always maintain contact, there is at most one such interval and it will be associated to the same compliant component.
5.2 Reverse compliant exploration
- Then c ′ c is the starting point for reverse compliant exploration.
- Since the edges in Tg are directed to the goal position, the paths that result from compliant exploration need to be directed to c′c.
- Stated differently, the authors want to know from which part of compliant space c′c is reachable.
- Since reverse exploration is used, the reverse exploration direction is counter clockwise for the paths that are directed clockwise (and vice versa).
- In contrast to forward exploration, using reverse exploration, two intervals may be reachable from Iγi .
5.3 Geometric Aspects
- Compliant exploration is a purely geometric process.
- The first can be found by calculating intersections between CS2ro+rp and CSrp. (b) An obstacle can also leave the push range.
- Using the events in the order in which they are encountered, it is easy to determine the chain of intervals that are reachable from the compliant start position in both the forward and reverse exploration direction.
- If O can be pushed completely around a single obstacle without any event occurring, an interval also ends.
6 Probabilistic completeness
- The basic RRT algorithm (that only grows a tree from the start configuration) is known to be probabilistically complete [14].
- The advantage of the bidirectional version of the RRT is that it helps escaping narrow passages.
- Because of the random nature of the RRT every pushable path through non compliant space will eventually be found.
- The above also means that every possible compliant configuration reachable from non compliant space will eventually be found, because a compliant section in a path is always preceded by a non-compliant section.
- Also since eventually every vertex will be generated, every hockey stick curve will be considered, and thus all possibilities to leave a compliant section will be tried.
7 Experiments
- The authors implemented their algorithm in Visual C++.
- Using the events, the list of intervals for every obstacle was created.
- With compliance, it is easy to reach the goal once a compliant configuration has been found.
- Preprocessing takes about 0.007s after which queries can be executed in 0.004s on average.
- After preprocessing which takes about 0.01s, their algorithm is able to find a path in 0.0005s on average as opposed to 0.01s for the RRT algorithm.
8 Conclusions
- In this paper the authors have introduced a novel manipulation planning algorithm in which pushing is combined with compliant motions.
- The resulting manipulation plans use compliance to extend the range of problems for which a solution can be created.
- The authors used the RRT algorithm to provide a natural balance between the number of compliant and non-compliant path segments.
- If the environment is preprocessed then, given a compliant configuration, it is easy to check to which interval that configuration belongs and thus what part of the compliant space is reachable from it using geometric operations.
- Extending their algorithm by allowing these non-contact transits can be done by using existing motion planning techniques in which the pusher moves and the object is considered an obstacle.
Did you find this useful? Give us your feedback
Figures (20)

Figure 4: The push range. The path of the object is shown by the dotted arrow. (a) The (counter clockwise) push range if no friction is assumed between the object and the obstacle. (b) The push range if there is friction between O and the obstacle. (c) The (clockwise) push range if O is pushed around an endpoint of an obstacle (no friction). (d) Pushing cannot continue because P is forced outside the push range by an obstacle. 
Figure 3: (a) An example of the compliant space CSro shown as the dotted lines. (b) The racetrack Rroγi of an obstacle γi. The position of O can be described by its compliant position. 
Figure 10: (a) A scene consisting of 4 obstacles. As can be seen from the compliant space CSro (the dotted lines), the top 3 obstacles form a compliant component while the bottom obstacle is a compliant component on its own. (b) Even though the two obstacles form a compliant component, the object runs into a dead-end. 
Table 1: Results of the experiments. 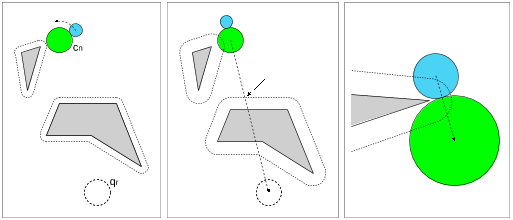
Figure 13: Ray shooting in the contact spaces. The rays are the dotted arrows. (a) A circular ray shoot in CSrp to collision check the contact transit. (b) A linear ray shoot in CSro to collision check the path of O. The arrow shows the point of collision. (c) A linear ray shoot in CSrp to collision check the wedges. 
Figure 19: (a) Experimentation scene. At the left the start configuration is shown, in the center the goal configuration. (b) An example of a final path, the dotted lines represent non-compliant path segments, the solid lines represent compliant path segments. 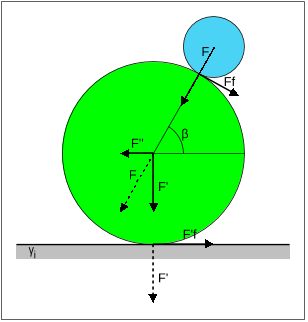
Figure 5: The role of friction on the behavior of O and P . F is the force applied by P on O. µ1 is the friction between O and γ, µ2 is the friction between O and P . 
Figure 6: Bounding obstacles. (a) If P rotates to either pr−b or pr − e it does not encounter any obstacle, therefore the bounding obstacles are (⊥,⊥). (b) P cannot reach pr−e , the bounding obstacles are (⊥, γ2). (c) The bounding obstacles are (γ3, γ2). 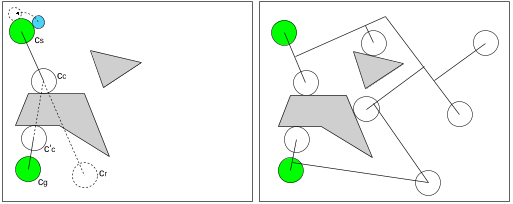
Figure 9: Example of the creation of an RRT. (a) The first iteration, the position of P is determined by the direction of the path from cs to cc. (b) The final RRT. As can be seen, a couple of compliant configurations have been found. 
Figure 12: (a) During the hockey stick push, P encounters an obstacle. (b) A second hockey stick is used. 
Figure 1: An example created by our implementation. At the left bottom the start configuration is shown. The object is pushed to the goal using a combination of compliant and non-compliant segments. The dotted line represents the path of the object. At some points the motion of the pusher is shown. 
Figure 16: Reverse exploration in the direction of the arrow. (a) At this point P has the choice between two intervals (either going clockwise or counterclockwise around γj). (b) If P chooses the counterclockwise direction, a small interval is reached. (c) If P chooses the path through the corridor between the two obstacles, a larger interval is reached. 
Figure 11: The different situations the local planner has to deal with, (a..c) are the situations of the forward local planner, (d..g) are the situations of the reversed local planner. Note that in the reversed local planner the edges in the tree are directed opposite to the dotted arrows that show the direction of exploration. 
Figure 7: The compliant intervals of the counterclockwise path on the racetrack of obstacle γ1. (a) Pushing O counterclockwise around γ1, every compliant position can be reached. The counterclockwise compliant positions are divided in 5 intervals. (b)...(f) The intervals of γ1. The respective bounding obstacles are: (⊥,⊥), (⊥, γ2), (⊥, γ3), (γ2,⊥) and (γ2, γ3). Note that the intervals of (c), (e) and (f) overlap. 
Figure 17: The various structures necessary to determine the events. All consist of circular arcs and straight lines. (a) CSrp. (b) CSro. (c) CS2rp+ro . (d) CS2ro+rp . (e) The path of the lowest position of the push range clockwise LPCW . (f) The path of the lowest position of the push range counterclockwise LPCCW . 
Figure 15: Compliant exploration ends. (a) O hits another obstacle and P is not able to reach the new push range. (b) P is forced outside the push range by an obstacle. (c) O has been pushed completely around a compliant component. 
Figure 8: (a) β is the initial angle between O and P . (b) The start situation, the target of O is shown as the dotted disk. (c) A hockey stick curve. The dotted lines show the paths of O and P . (d) A hockey stick push. First a hockey stick curve is used, followed by a straight line push. The resulting path is the shortest path to the goal from the start configuration. 
Figure 18: The various events that trigger the start and end of intervals. 
Figure 2: Three examples in which compliance helps finding a push plan for a disk pushing another disk. The top figures show the path toward the goal with a dotted arrow. The bottom figures show the solutions if compliance is allowed. 
Figure 14: The subintervals are associated to a vertex. (a) The dotted arrow shows how O arrived on the interval. From that position, P is guaranteed to be able to push O to the end of the interval (qe), hence the subinterval that is associated to a vertex v. (b) If, at a later moment, O arrives in an already explored part of the interval, no new vertex needs to be added to Ts. (c) If O arrives in a not previously explored part of the interval, the subinterval is extended.
Citations
14 citations
Cites methods from "Pushing using compliance"
...[9, 11, 12] developed a probabilistically complete algorithm for this based on the Rapidly-exploring Random Trees path-planning algorithm [6]....
[...]
9 citations
Cites methods from "Pushing using compliance"
...[9, 11, 12] developed a probabilistically complete algorithm for this based on the Rapidly-exploring Random Trees path-planning algorithm [6]....
[...]
6 citations
3 citations
Cites background from "Pushing using compliance"
...Samplingbased motion planning for compliant robots has been previously explored in [19], albeit limited to disc robots with simplified contact behavior....
[...]
1 citations
Cites background from "Pushing using compliance"
...Sampling-based motion planning for compliant robots has been previously explored in [77], albeit limited to disc robots with simplified contact behavior....
[...]
References
[...]
7,315 citations
7,159 citations
6,340 citations
3,102 citations
"Pushing using compliance" refers background in this paper
...The results of this compliant exploration are added as configurations to the tree....
[...]