




Did you find this useful? Give us your feedback

























946 citations
...Index Terms—Mobile sensor networks, sensor coverage, distributed algorithm....
[...]
817 citations
582 citations
...Permission to make digital or hard copies of all or part of this work for personal or classroom use is granted without fee provided that copies are not made or distributed for pro.t or commercial advantage and that copies bear this notice and the full citation on the .rst page....
[...]
536 citations
...For example, the work in [ 24 ] assumes that a powerful cluster head is available to collect information and determine the target location of the mobile sensors....
[...]
...This sensor relocation is different from existing work on mobile sensors which concentrate on sensor deployment; i.e., moving sensors to provide certain initial coverage [11], [12], [20], [21], [ 24 ]....
[...]
523 citations
...The simulation result of Zou and Chakrabarty (2003) shows that a sensor deployment technique based on virtual forces can increase the area coverage after an initial random deployment....
[...]
...Zou and Chakrabarty (2003) assumes that obstacles exert repulsive (negative) forces on a sensor....
[...]
4,123 citations
...Radar and sonar coverage also present several related challenges [13]....
[...]
...Based on the measured radar cross-sections and the coverage diagrams for the different radars, the authors in [13] propose a method for optimally locating the radars to achieve satisfactory surveillance with limited radar resources....
[...]
1,837 citations
...The problem of evaluating the coverage provided by a given placement of sensors is discussed in [7]....
[...]
1,547 citations
...Finally, there exists a close resemblance between the sensor placement problem and the art gallery problem (AGP) addressed by the art gallery theorem [14]....
[...]
1,273 citations
...The VFA algorithm combines the ideas of potential field [5] and disk packing [11]....
[...]
...The deployment of sensors for coverage of the sensing field has been considered for multi-robot exploration [5]....
[...]
...The VFA algorithm is inspired by disk packing theory [11] and the virtual force field concept from robotics [5]....
[...]
956 citations
...Sensor placement on two- and three-dimensional grids has been formulated as a combinatorial optimization problem, and solved using integer linear programming in [3], [4]....
[...]
...Equation (1) shows the binary sensor model [3], [4] that expresses the coverage cxy(si) of a grid point P by sensor si....
[...]
Their future work will be focused on overcoming the current limitations of the VFA algorithm. Since the current target localization algorithm considers only one target in the sensor field, it is necessary to extend the proposed approach to facilitate the localization of multiple objects. Extensions to non-mobile sensor nodes, and situations of sensor node failures will also be considered in future work. The VFA algorithm can be made more efficient if it is provided with the theoretical bounds on the number of sensors needed to achieve a given coverage threshold.
In order to conserve power and bandwidth, the message from the sensor to the cluster head is kept very small; in fact, the presence or absence of a target can be encoded in just one bit.
the desired sensor field coverage and model parameters can be provided as inputs to the VFA algorithm, thereby ensuring flexibility.
The cluster head is responsible for executing the VFA algorithm and managing the one-time movement of sensors to the desired locations.
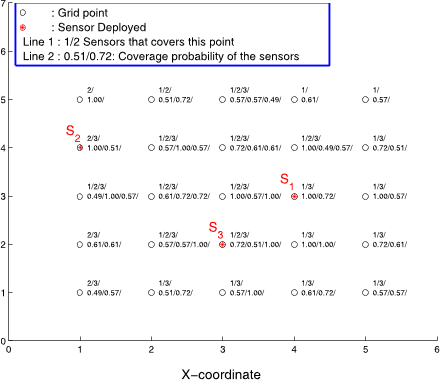
Each sensor has a detection radius as 5 units (r = 5), and range detection error as 3 units (re = 3) for the probabilistic detection model.
This ensures that the detection regions of two sensors do not overlap, thereby minimizing “wasted overlap” and allowing us to cover a large grid with a small number of sensors.
After the VFA algorithm is used to determine the final sensor locations, the cluster head generates a detection probability table for each grid point.
Since the term (1− cx,y(si))(1− cx,y(sj)) expresses the probability that neither si nor sj covers grid point at (x, y), the probability that the grid point (x, y) is covered is given by Equation (5).
The set Srep(t) indicates sensors that have reported the detection at time instant t. The set Sq(t) includes sensors that are selected for querying by the cluster head at time t.