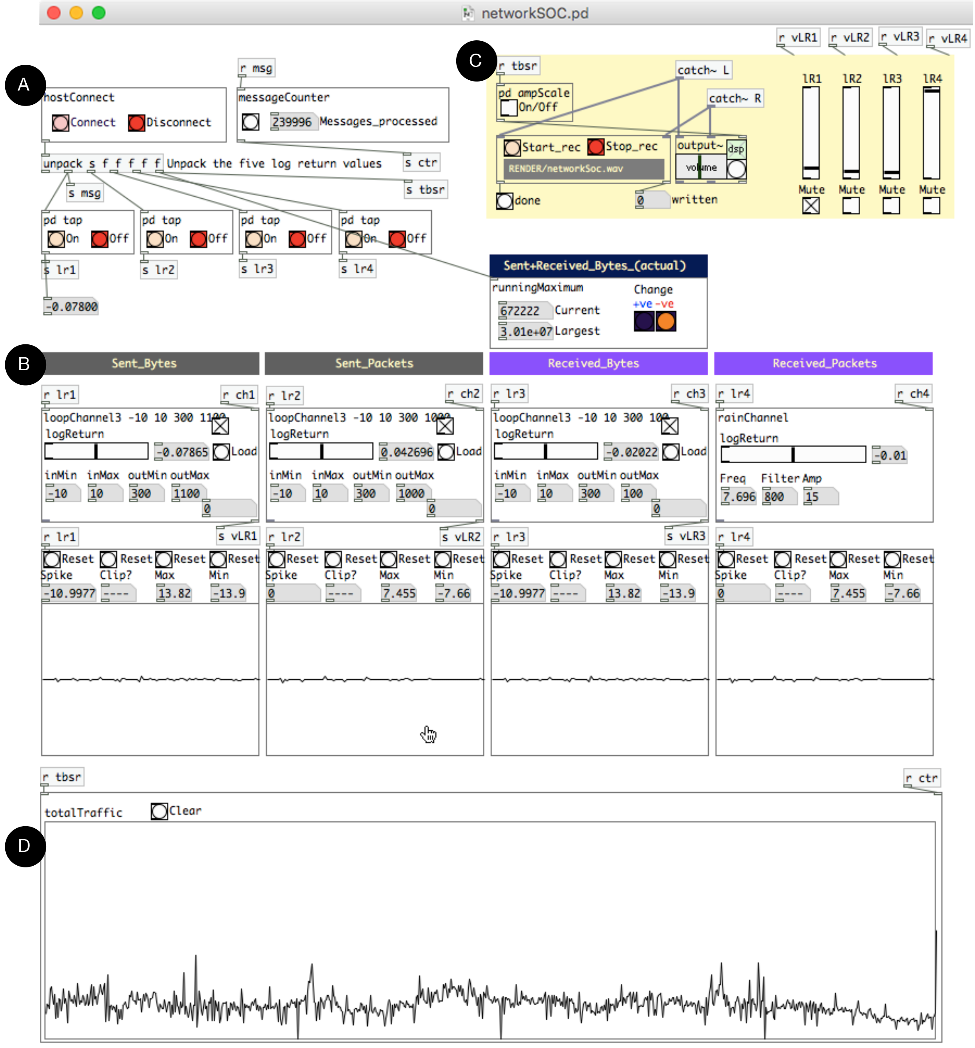
Abstract: INTRODUCTION Historically, an enormous amount of research and development on information fusion has been conducted in support of military operations (e.g., fusion of multi-sensor data for target tracking, identification, and threat assessment and situation awareness) (Hall and McMullen, 2004) (Liggins et al., 2008). The research has included development of process models, creation of algorithms for signal and image processing, pattern recognition , state estimation, automated reasoning, and dynamic resource allocation. ABSTRACT Computer networks no longer simply enable military and civilian operations, but have become vital infrastructures for all types of operations ranging from sensing and command/control to logistics, power distribution, and many other functions. Consequently, network attacks have become weapons of choice for adversaries engaged in asymmetric warfare. Traditionally, data and information fusion techniques were developed to improve situational awareness and threat assessment by combining data from diverse sources, and have recently been extended to include both physical (" hard ") sensors and human observers (acting as " soft " sensors). This chapter provides an introduction to traditional data fusion models and adapts them to the domain of cyber security. Recent advances in hard and soft information fusion are summarized and applied to the cyber security domain. Research on the use of sound for human-in-the-loop pattern recognition (sonification) is also introduced. Finally, perspectives are provided on the future for data fusion in cyber security research. This chapter adapts these models to the domain of cyber security. This is a field in which data fusion techniques and terminology are becoming increasingly relevant, given the complex tasks of maintaining overall awareness of a network's current status, projecting future actions of adversaries , and making timely adjustments. Following a discussion of hard and soft information fusion and their relevance to the cyber security domain, we propose a novel means of situational awareness involving an auditory representation (sonification) of network traffic. This chapter is organized as follows. We begin by exploring of some of the background research in three areas of interest – use of humans as soft sensors, data fusion technologies in cyber security , and sonification. The first content area of human-centric information fusion outlines the use of humans as " soft " sensors. The second content area presents the general data fusion framework (the JDL model) as it applies to the cyber security context. The third main content area, sonification, is construed as a cognitive refinement. The chapter concludes with a …