
")%&'+#"'(+
"#*
6/795*;276%,2.6,.*,<4;?"<+42,*;276: 6/795*;276%,2.6,.
Lightweight &ree-Factor Authentication and Key
Agreement Protocol for Internet-Integrated
Wireless Sensor Networks
Qi Jiang
Xidian University, China
Sherali Zeadally
University of Kentucky:@.*-*44?<3?.-<
Jianfeng Ma
Xidian University, China
Debiao He
Wuhan University, China
' '##$"#%!""*''# '(&"#*#*'&#(!"'"-'&+#(
7447>;12:*6-*--2;276*4>793:*; 1C8:<367>4.-0.<3?.-<:42:)/*,8<+
"*9;7/;1. 202;*4755<62,*;276:*6-!.;>79326075576:*6-;1. 6/795*;276%.,<92;?
75576:
B2:9;2,4.2:+97<01;;7?7</79/9..*6-78.6*,,.::+?;1.6/795*;276%,2.6,.*;&67>4.-0.;1*:+..6*,,.8;.-/7926,4<:276266/795*;276
%,2.6,.*,<4;?"<+42,*;276:+?*6*<;1792@.-*-5262:;9*;797/&67>4.-0.79579.26/795*;27684.*:.,76;*,; &67>4.-0.4:=<3?.-<
$.87:2;79?2;*;276
2*60#2(.*-*44?%1.9*42 *2*6/.60*6-..+2*7201;>.201;B9..*,;79<;1.6;2,*;276*6-.?09..5.6;"97;7,74/79
6;.96.;6;.09*;.-'29.4.::%.6:79!.;>793: Information Science Faculty Publications
1C8:<367>4.-0.<3?.-<:42:)/*,8<+

'*',%'#%('"''#""+%!"'%#'## #%"'%"'"'%'% &&"&#%
'*#%&
#'&''#""#%!'#"
"<+42:1.-26 IEEE Access=8
A
B.,78?9201;174-.91*:09*6;.-;1.8.952::276/7987:;260;1.*9;2,4.1.9.
' '"'-%
1C8:-72790%%
B2:*9;2,4.2:*=*24*+4.*;&67>4.-0. 1C8:<367>4.-0.<3?.-<:42:)/*,8<+

SPECIAL SECTION ON SECURITY AND PRIVACY IN APPLICATIONS AND SERVICES FOR
FUTURE INTERNET OF THINGS
Received January 29, 2017, accepted February 14, 2017, date of publication March 3, 2017, date of current version March 28, 2017.
Digital Object Identifier 10.1109/ACCESS.2017.2673239
Lightweight Three-Factor Authentication and Key
Agreement Protocol for Internet-Integrated
Wireless Sensor Networks
QI JIANG
1
, SHERALI ZEADALLY
2
, JIANFENG MA
1
, AND DEBIAO HE
3,4
1
School of Cyber Engineering, Xidian University, Xi’an 710071, China
2
College of Communication and Information, University of Kentucky, Lexington, KY 40506-0224, USA
3
Software Engineering, Wuhan University, Wuhan 430072, China
4
School of Computer and Software, Nanjing University of Information Science and Technology, Nanjing 210044, China
Corresponding author: Q. Jiang (jiangqixdu@gmail.com)
This work was supported in part by the National Science Foundation of China under Grant 61672413, Grant 61572379, Grant 61501333,
Grant U1405255, Grant 61372075, and Grant U1536202, in part by the Natural Science Basic Research Plan in Shaanxi Province of China
under Grant 2016JM6005, in part by Fundamental Research Funds for the Central Universities under Grant JB161501 and
Grant JBG161511, in part by the National High Technology Research and Development Program (863 Program) of China under
Grant 2015AA016007, and in part by the China 111 Project under Grant B16037.
ABSTRACT Wireless sensor networks (WSNs) will be integrated into the future Internet as one of the
components of the Internet of Things, and will become globally addressable by any entity connected to the
Internet. Despite the great potential of this integration, it also brings new threats, such as the exposure of
sensor nodes to attacks originating from the Internet. In this context, lightweight authentication and key
agreement protocols must be in place to enable end-to-end secure communication. Recently, Amin et al.
proposed a three-factor mutual authentication protocol for WSNs. However, we identified several flaws in
their protocol. We found that their protocol suffers from smart card loss attack where the user identity and
password can be guessed using offline brute force techniques. Moreover, the protocol suffers from known
session-specific temporary information attack, which leads to the disclosure of session keys in other sessions.
Furthermore, the protocol is vulnerable to tracking attack and fails to fulfill user untraceability. To address
these deficiencies, we present a lightweight and secure user authentication protocol based on the Rabin
cryptosystem, which has the characteristic of computational asymmetry. We conduct a formal verification
of our proposed protocol using ProVerif in order to demonstrate that our scheme fulfills the required security
properties. We also present a comprehensive heuristic security analysis to show that our protocol is secure
against all the possible attacks and provides the desired security features. The results we obtained show that
our new protocol is a secure and lightweight solution for authentication and key agreement for Internet-
integrated WSNs.
INDEX TERMS Authentication, biometrics, key management, privacy, Rabin cryptosystem, smart card,
wireless sensor networks.
I. INTRODUCTION
One vision of future Internet is that objects and things with
sensing and actuating capabilities will be connected and inte-
grated making up the Internet of Things (IoTs). As Wire-
less Sensor Network (WSN) is one of the core technologies
supporting the sensing capabilities required by future appli-
cations, the integration of WSN with the Internet will have
an active role in the evolution of the architecture of future
Internet [1]–[3]. The Internet Engineering Task Force (IETF)
has developed a suite of protocols and open standards for
integrating WSN into Internet [4], such as 6LoWPAN [5] and
ROLL [6]. As illustrated in Fig. 1, sensor nodes (SNs) can be
connected by low rate and low power wireless technologies
such as IEEE 802.15.4, and can be further linked to the
Internet via a 6LoWPAN gateway. Therefore, sensors will be
globally addressable by any entity connected to the Internet
thereby enabling the remote access of sensor data.
Despite its great potential, the integration of WSN with
the Internet also brings new threats, such as the exposure
of resource-constrained SNs and low rate wireless links in
3376
2169-3536 2017 IEEE. Translations and content mining are permitted for academic research only.
Personal use is also permitted, but republication/redistribution requires IEEE permission.
See http://www.ieee.org/publications_standards/publications/rights/index.html for more information.
VOLUME 5, 2017
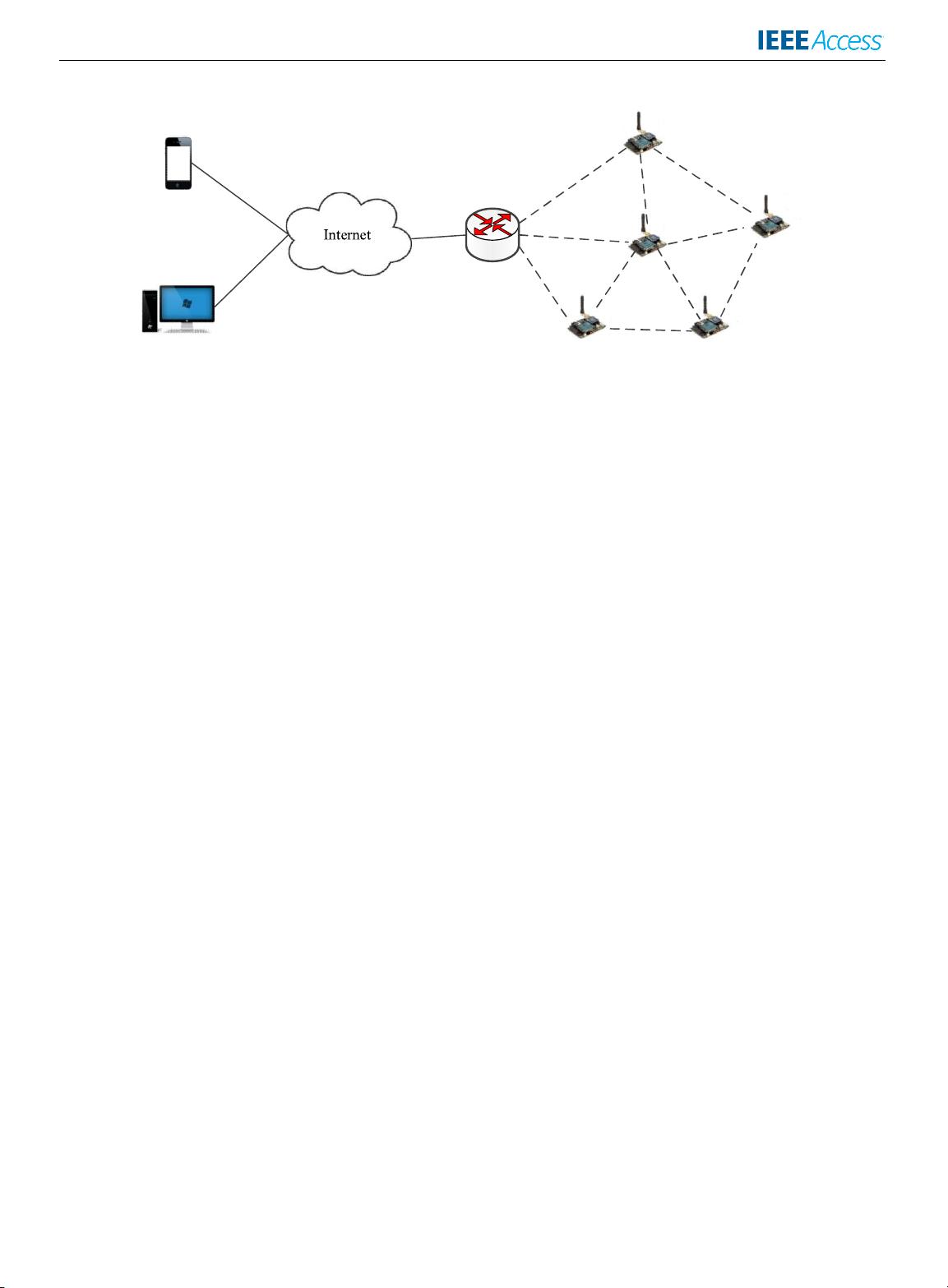
Q. Jiang et al.: Lightweight Three-Factor Authentication and Key Agreement Protocol
FIGURE 1. Typical architecture of Internet integrated wireless sensor networks.
WSN to attacks emanating from the Internet [3], [7]–[12].
Given its sensitivity and criticality, the sensor data in transit
must be protected by an end-to-end (E2E) secure channel
between the SN and the entity outside the WSN. The creation
of such a channel requires authentication and key agree-
ment mechanisms that allow two remote entities to mutually
authenticate and negotiate secret keys that are used to protect
the sensor data against various types of active and passive
attacks [2], [13], [14]. Note that even if the WSN itself has
security measures at a lower layer such as the link layer
security services defined by IEEE 802.15.4, the openness of
the Internet still requires authentication and key agreement
protocols for establishing the E2E secure channel between
the two communicating peers [2].
It is not possible to directly utilize Internet-centric security
solutions because of the inherent characteristics of WSN
(e.g., the limited computational capabilities and power supply
of sensors and mobile devices) [2]. As discussed in [15],
many attempts (for instance, IPsec [16], IKEv2 [17]) have
been made to adapt standard Internet security protocols in this
scenario.
However, resource limitation and the large number of SNs
hinder the adoption of these solutions. Therefore, it is imper-
ative to enable authentication and key establishment between
the SN and the entity outside WSN in a secure and lightweight
manner. However, past experiences [18]–[20] have shown
that it is not trivial to design such security protocols.
A. RELATED WORKS
In the last decade, various security mechanisms [7],
[21]–[25] have been proposed to prevent unauthorized access
to the sensor data in transit. Li and Xiong [24] proposed a
signcryption scheme to protect the information flow between
a sensor and an entity outside the WSN, which fulfills con-
fidentiality, integrity, authentication, and non-repudiation in
one step. However, bilinear pairing is used in the scheme,
which makes it unsuitable (because of its high computation
and processing overheads) for regular SNs.
Astorga et al. [25] proposed the Ladon security
protocol which provides E2E authentication and key
establishment mechanism for resource-constrained devices.
To prevent potential eavesdroppers from tracking users’
access patterns, they also presented a privacy-enhanced
Ladon protocol by integrating the original protocol with the
PrivaKERB user privacy framework for Kerberos [7]. In these
protocols, the long keys need to be securely stored and may
be compromised.
To improve WSN security, two-factor authentication (2FA)
protocols [26] have been introduced in WSN. In such pro-
tocols, two different types of security credential are used,
i.e., smart card and password, to prove his/her identity. Over
a dozen of 2FA schemes for WSNs have been proposed in
recent years [18]–[20], [27]–[31]. We briefly review the ones
closest to this work.
In 2014, Turkanovic et al. [32] proposed a lightweight
2FA protocol based on hash function for WSNs, which
is claimed to be energy efficient and secure. However,
Amin and Biswas [33] showed that the protocol of
Turkanovic et al. [32] has several security weaknesses,
including offline identity guessing attack, offline password
guessing attack, impersonation attack, etc. To address these
security deficiencies, they proposed a 2FA protocol for multi-
gateway WSN. Independently, Farash et al. [34] also revealed
that the protocol of Turkanovic et al. [32] is susceptible to
smart card loss attacks (SCLA), impersonation attack, session
key disclosure, et al. and proposed an improved 2FA proto-
col. In the same year, Chang and Le [35] demonstrated that
the 2FA protocol by Turkanovic et al. [32] is prone to SN
spoofing attack, stolen smart card attack, and stolen verifier
attack, et al. Then they proposed two 2FA protocols P1 and
P2 [37]. P1 is based on hash functions, while P2 employs
Elliptic Curve Cryptography (ECC).
Lu et al. [36] analyzed Amin-Biswas’s 2FA protocol [33]
and identified several security drawbacks in their protocol.
Next, they proposed an enhanced 2FA scheme using sym-
metric key cryptography, which is claimed to be resilient to
a variety of attacks. Wu et al. [37] also pointed out that the
2FA protocol of Amin and Biswas [33] is insecure. Most
recently, Das et al. [38] showed that both P1 and P2 by Chang
and Le [35] are vulnerable to session specific temporary
VOLUME 5, 2017 3377

Q. Jiang et al.: Lightweight Three-Factor Authentication and Key Agreement Protocol
information attack and offline password guessing attack, etc.
Amin et al. [39] found that the protocol of Farash et al. [34]
cannot provide user anonymity, or withstand SCLA, offline
password guessing attack, user impersonation attack, known
session-specific temporary information attack (KSSTIA).
To address the vulnerabilities associated with the various
2FA approaches and further enhance the security strength
of 2FA protocols, three-factor authentication (3FA) proto-
cols have attracted the attention of researchers [40]–[44].
In the context of WSN, Das [45] presented a 3FA protocol
based on symmetric cryptographic primitives. Next, he also
proposed two other 3FA protocols [46]–[47]. Unfortunately,
Wu et al. [48] demonstrated that all the three protocols are not
secure. To address the drawbacks, they proposed an improved
3FA scheme based on ECC. Independently, Li et al. [49]
presented a novel 3FA protocol based on the concept of
biohashing. However, Das et al. [50] demonstrated that the
protocol of Li et al. [49] is vulnerable to privileged insider
attack, SN capture attack and cannot provide user anonymity.
Most recently, to remedy these security loopholes in the
protocol of Farash et al. [34], Amin et al. [39] presented a new
secure 3FA protocol, which is claimed to be secure against all
the known security attacks. Additionally, to satisfy the practi-
cal requirements, their protocol provides the functionalities of
post deployment, identity update, password update, and smart
card revocation. However, we observe that the protocol by
Amin et al. still has some subtle security weaknesses.
B. OUR RESEARCH CONTRIBUTIONS
Although several 3FA protocols [38], [39], [45]–[49] have
been proposed in the literature, all these protocols either fail
to provide adequate security protection or suffer from various
security vulnerabilities. In this paper, we use the most recent
3FA protocol of Amin et al. [39] as a case study to show the
challenge of designing a lightweight authentication protocol
suitable for Internet integrated WSN. Then we propose an
authentication protocol for Internet integrated WSN which
exploits the computational asymmetry feature of Rabin cryp-
tosystem. We summarize our main research contributions as
follows:
• First, we analyze the most recent 3FA protocol of Amin
et al. [39] and we present its security drawbacks. Specif-
ically, we found that their protocol suffers from Type I
SCLA (the secret data obtained from the smart card is
enough for an adversary to reveal the user password) and
Type II SCLA (the transcripts of an authentication ses-
sion are needed for an attacker, in addition to the secret
parameters in the user’s smart card). Specifically, the
user identity and password can be exhaustively guessed
in an offline manner along with the secrets stored in the
stolen smart card and the intercepted authentication mes-
sages. Additionally, the protocol suffers from KSSTIA if
the temporal parameters in an authentication session are
disclosed. Furthermore, the protocol is prone to tracking
attack and cannot fulfill user untraceability.
• Second, we present an efficient and secure 3FA protocol
based on the Rabin cryptosystem. Unlike other public
key-based encryption algorithms such as RSA and ECC,
Rabin has the characteristic of computational asymme-
try. In this case, the encryption is very efficient while
the decryption is relatively heavyweight. This feature
is particular well suited for Internet integrated WSN
because the mobile device of users is generally resource-
constrained while the gateway has no such restriction.
• Third, we conducted a formal verification using
ProVerif [51] to demonstrate that our protocol fulfills
the required security features. Furthermore, we also
present comprehensive heuristic security analysis to
demonstrate that our protocol is capable of withstand-
ing all the possible active and passive attacks includ-
ing the security weaknesses revealed in the protocol of
Amin et al., and we show how it provides the desired
security features. Additionally, performance analysis
shows that our proposed protocol is a practical solution
that can provide authentication and key agreement for
Internet integrated WSN, while achieving both security
and efficiency.
The remainder of this paper is organized as follows. The
preliminaries of Biohashing and Rabin cryptosystem are
given in Section 2. We review and analyze Amin et al.’s
protocol [39] in Section 3 and 4 respectively. In Section 5, we
propose a novel 3FA and key agreement protocol for Internet
integrated WSN. Section 6 and Section 7 present security and
efficiency analyses of the new protocol. Section 8 concludes
the paper.
II. PRELIMINARY
A. BIOHASHING
Biometric is widely used to verify the identity of a user.
It offers several advantages over traditional authentication
methods, i.e., password and smart card. Biometric feature
data is closely coupled with each individual and cannot be
replaced. As a result, the disclosure of biometric data leads to
serious privacy risks. Numerous schemes have been proposed
to preserve the privacy of biometric template [52]–[55].
Biohashing [55], [56] is one of the mainstream privacy-
preserving biometric schemes. In the enrollment stage, a
biohash value BH (K , B) is generated from the biometric
template B and a random secret key K . Specifically, a pre-
processing is performed on B in order to make the biometric
feature invariant to small variations in the input biometric
signal. Then, the biohash value BH (K, B) is generated by
comparing the inner product of the random vector generated
from the user specific secret key K and the feature vector
extracted against a predefined threshold. In the verification
stage, by following the process used at the enrolment stage, a
biohash value BH (K, B
′
) can be generated from the received
biometric signal B
′
and the secret key given by the user.
Afterwards, the verification is done by comparing BH (K , B
′
)
with the stored value BH(K, B) [52].
3378 VOLUME 5, 2017