Novel blind multiple watermarking technique for images
TLDR
Experimental results show that embedded watermarks using the proposed techniques can give good image quality and are robust in varying degree to JPEG compression, low-pass filtering, noise contamination, and print-and-scan.Abstract:
Three novel blind watermarking techniques are proposed to embed watermarks into digital images for different purposes. The watermarks are designed to be decoded or detected without the original images. The first one, called single watermark embedding (SWE), is used to embed a watermark bit sequence into digital images using two secret keys. The second technique, called multiple watermark embedding (MWE), extends SWE to embed multiple watermarks simultaneously in the same watermark space while minimizing the watermark (distortion) energy. The third technique, called iterative watermark embedding (IWE), embeds watermarks into JPEG-compressed images. The iterative approach of IWE can prevent the potential removal of a watermark in the JPEG recompression process. Experimental results show that embedded watermarks using the proposed techniques can give good image quality and are robust in varying degree to JPEG compression, low-pass filtering, noise contamination, and print-and-scan.read more
Figures

Fig. 30. (Left) MWE-watermarked image under LPF attack.PSNR = 31:82 dB. (Middle) Decoded watermark. (Right) Random watermark detection results. 
Fig. 26. Detection error of MWE under LPF attack. 
Fig. 6. (a) Original logo “UST”. (b)-(f) Original logo “Alphabet”. 
Fig. 23. Distribution ofS of MWE (IA-R, Q = 5) under JPEG attack. 
Fig. 28. Detection error of MWE under noise attack. 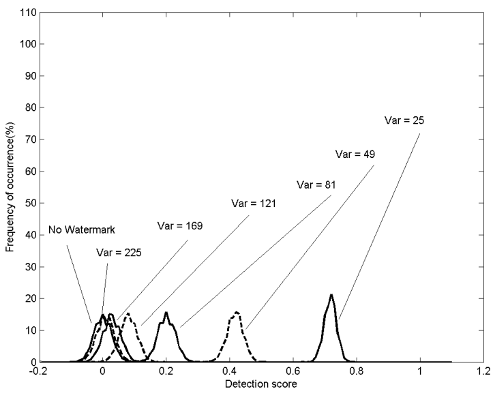
Fig. 27. Distribution ofS of MWE under noise attack.
Citations
More filters
Proceedings ArticleDOI
Novel Method for Key Storage Systems
Huong Thi Nguyen,Hung Quang Ta +1 more
TL;DR: Wang et al. as mentioned in this paper proposed a new method for accessing and storing private keys using advanced features of watermarking and symmetric encryption, the shared private key slices are encrypted and stored in different boxes, and the entire private key is reconstructed as long as the boxes are effective.
Proceedings ArticleDOI
Security in collaborative multimedia art communities
TL;DR: The strength of this system considers multimedia content not as an atomic digital entity, but as a part of a project with a specific workflow that applies watermarking techniques in all its parts.
Proceedings ArticleDOI
Enhancing Robustness and Imperceptibility of Blind Watermarking with Improved Message Processor
TL;DR: Wang et al. as discussed by the authors proposed an improved blind watermarking method by using an improved message processor with sub-pixel convolution layers and low-frequency features and incorporating double discriminators to improve the performance of the network.
Journal Article
Two Dimensional Data Hiding using Haar Wavelet Filter
TL;DR: In this article, two dimensional data hiding using Haar Wavelet filter has been proposed, secret data is secured by Discrete Wavelet Transform (DWT) which is embedded into the mid frequency subband of a cover data by using variable mixing factor (k).
Book ChapterDOI
A watermarking algorithm for JPEG file
TL;DR: Wang et al. as discussed by the authors proposed a watermarking algorithm working directly on JPEG bit-stream, which embeds watermark bits by modifying de-quantized DC coefficients.
References
More filters
Journal ArticleDOI
Secure spread spectrum watermarking for multimedia
TL;DR: It is argued that insertion of a watermark under this regime makes the watermark robust to signal processing operations and common geometric transformations provided that the original image is available and that it can be successfully registered against the transformed watermarked image.
Book
Digital Watermarking
TL;DR: Digital Watermarking covers the crucial research findings in the field and explains the principles underlying digital watermarking technologies, describes the requirements that have given rise to them, and discusses the diverse ends to which these technologies are being applied.
Journal ArticleDOI
Hidden digital watermarks in images
Chiou-Ting Hsu,Ja-Ling Wu +1 more
TL;DR: The experimental results show that the proposed image authentication technique by embedding digital "watermarks" into images successfully survives image processing operations, image cropping, and the Joint Photographic Experts Group lossy compression.
Journal ArticleDOI
DCT-domain watermarking techniques for still images: detector performance analysis and a new structure
TL;DR: Analysis of a spread-spectrum-like discrete cosine transform (DCT) domain watermarking technique for copyright protection of still digital images is analyzed and analytical expressions for performance measures are derived and contrasted with experimental results.
Journal ArticleDOI
Rotation, scale, and translation resilient watermarking for images
TL;DR: It is shown that the watermark is robust to rotation, scale, and translation, and tests examining the watermarks resistance to cropping and JPEG compression.